MAC address vs IP address: What’s the difference?
MAC address vs IP address: One is a unique hardware identifier, while the other identifies a device’s network connection. Learn more with BlueCat.

Sorting through the definition of MAC address vs IP address can get a little confusing. They both relate to networking and they both have the word “address” in their names.
But they are, in fact, two different things.
A Media Access Control address (MAC address) is a hardware identifier that uniquely identifies each device on a network. Primarily, the manufacturer assigns it. They are often found on a device’s network interface controller (NIC) card. A MAC address can also be referred to as a burned-in address, Ethernet hardware address, hardware address, or physical address.
Meanwhile, an internet service provider (ISP) or network administrator assigns an Internet Protocol address (IP address). Associated with the TCP/IP protocol, an IP address helps identify a device connected to a network.
This post will explore the key differences between a MAC address vs IP address. Further, it will delve into how the two address types work together and how they’re used in the enterprise context. Finally, it will touch on how BlueCat can help with more efficient MAC and IP address management.
MAC address vs IP address: key differences
One is permanent, the other dynamic
Because they are assigned to NICs or other hardware, MAC addresses never change on their own. (But many network interfaces support MAC address changes.) On the other hand, many IP addresses are dynamic, changing periodically based on time or the particulars of a networking setup.
Unique address structures
A MAC address is a 48-bit hexadecimal address. It’s usually six sets of two digits or characters, separated by colons. An example MAC address would be 00:00:5e:00:53:af.
Many network card and other hardware manufacturers use a unique sequence at the beginning of their products’ MAC addresses. This is called an organizationally unique identifier (OUI). The OUI is usually the first three bytes of digits or characters. The IEEE (Institute of Electrical and Electronics Engineers) administers manufacturers’ OUIs.
Meanwhile, an IPv4 address is a 32-bit integer expressed in hexadecimal notation. The more common format, known as dotted quad or dotted decimal, is x.x.x.x, where each x can be any value between 0 and 255. For example, 192.0.2.146 is a valid IPv4 address.
Residing in different layers in the OSI model
A MAC address and IP address also sit in different layers of the Open Systems Interconnection (OSI) model. (The OSI model is a conceptual framework that uses seven abstraction layers to describe all the functions of a telecommunication system.) In the OSI model, the MAC sublayer of the data-link layer (Layer 2) implements MAC addresses. Meanwhile, an IP address operates in the network layer (Layer 3) of the model.
How a MAC address and IP address work together
The bridge between them: ARP
While MAC and IP addresses have many differences, they are not islands unto themselves. The Address Resolution Protocol (ARP) is the bridge that connects them. This protocol works between Layer 2 and Layer 3 on a local area network (LAN). It maps IPv4 addresses to network devices’ MAC addresses and vice versa.
(Note: IPv4 uses the ARP protocol. On newer IPv6 networks, the Neighbor Discovery Protocol provides the equivalent functionality.)
Here’s how it works: A device wants to communicate with another device on the local network segment. It puts its request with both the source IP address and a destination IP address into an IP packet. An Ethernet frame then encapsulates the IP packet. The frame contains both a source and destination MAC address as well.
But sometimes the MAC address of the destination device is unknown. In steps ARP.
Computer A and computer B example
Computer A wants to send an IP packet to computer B. But it does not know the MAC address of computer B. Computer A will then broadcast an ARP request received by all computers on the local network segment.
The request will essentially say, “This is my IP address. This is my MAC address. And I am looking for the MAC address associated with this IP address. If this IP address is yours, please respond and give me your MAC address.”
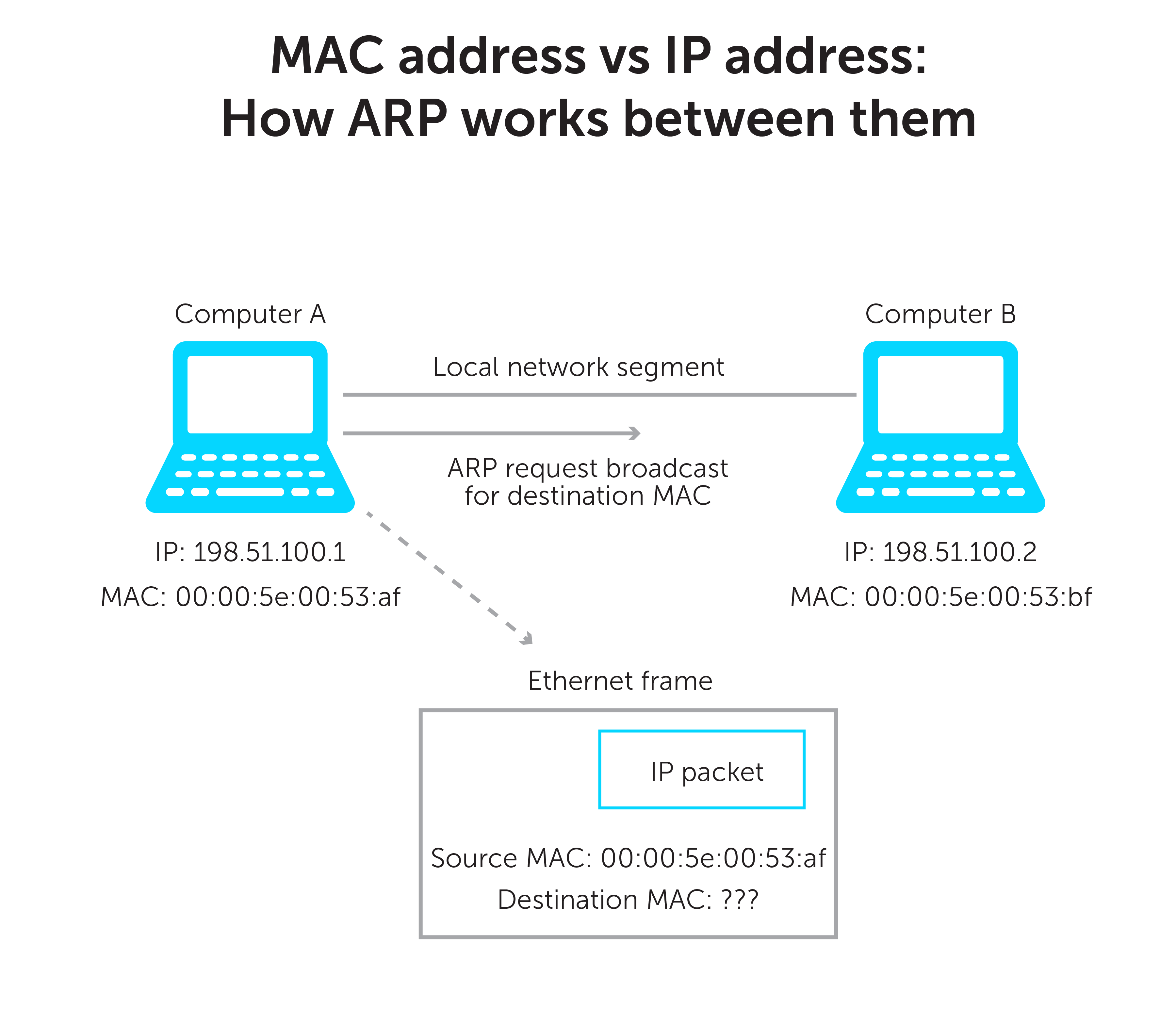
Computer B receives the ARP request and will do two things.
First, every device has its own ARP table. Each time a computer wants to send a packet on the LAN, it will look in its ARP table first. If an entry for Computer A does not already exist in Computer B’s table, it will make one. It will add computer A’s MAC and IP addresses based on what is in the frame.
Then, it will send an ARP reply with its IP address and MAC address. Computer A will receive the reply and add the info to its ARP table. With the right MAC address, Computer A can now send the Ethernet frame to Computer B.
It’s worth noting that, while an IP address is easy for anyone to look up, a MAC address can’t easily be found by others. Once an IP packet leaves your LAN and goes through a router, its header with the MAC address is stripped away. Therefore, anyone outside your LAN never sees your MAC in the IP packet (unless an application sends it as data).
Managing MAC addresses and IP addresses in the enterprise
MAC addresses and IP addresses are ubiquitous. For large enterprises, they can number in the millions. Certainly, there are some things IT enterprises can do to manage them most efficiently in their day-to-day operations.
Some enterprises still use IP address spreadsheets to manage all the IP addresses on their network, while often overlooking MAC addresses. But gambling with spreadsheets for IP address management (IPAM) can be a huge risk—with potentially catastrophic results. Excel spreadsheets were never intended to manage network infrastructure.
Unifying DNS, DHCP, and IPAM with BlueCat
A Domain Name System (DNS) and IP addresses go hand in hand. The primary purpose of DNS is to resolve human-readable domain names to machine-readable IP addresses. And Dynamic Host Configuration Protocol (DHCP) is the standard mechanism to dynamically assign addresses within a network.
Unifying management of your DNS, DHCP, and IPAM (together known as DDI) infrastructure can give you centralized visibility and control over these core network services. With BlueCat’s platform, you get a single source of truth for relationships between devices, users, and IP addresses on your network.
By seeing these relationships, network teams get full visibility into all their network traffic and can even identify cybersecurity threats faster. With BlueCat’s platform, you can systematically gather and analyze all your internal and external DNS data.
Furthermore, BlueCat Address Manager also allows admins to enter MAC addresses. MAC pools can group MAC addresses together for functionality. Each MAC address can be linked to multiple IP addresses of different networks. This can help administrators troubleshoot at the device level, giving them another tool for central visibility and management of network activity.






