MTK bootloader startup process
tags: MTK
1, bootloader to kernel start total logic flow chart
ARMArchitectureIn EL0/EL1, EL2/EL1 is required, EL2/EL3 is optional, and ELx is hierarchically related:
EL0 -- app
EL1 -- Linux kernel 銆乴k
EL2 -- hypervisor (virtualization)
EL3 -- ARM trust firmware 銆乸re-loader
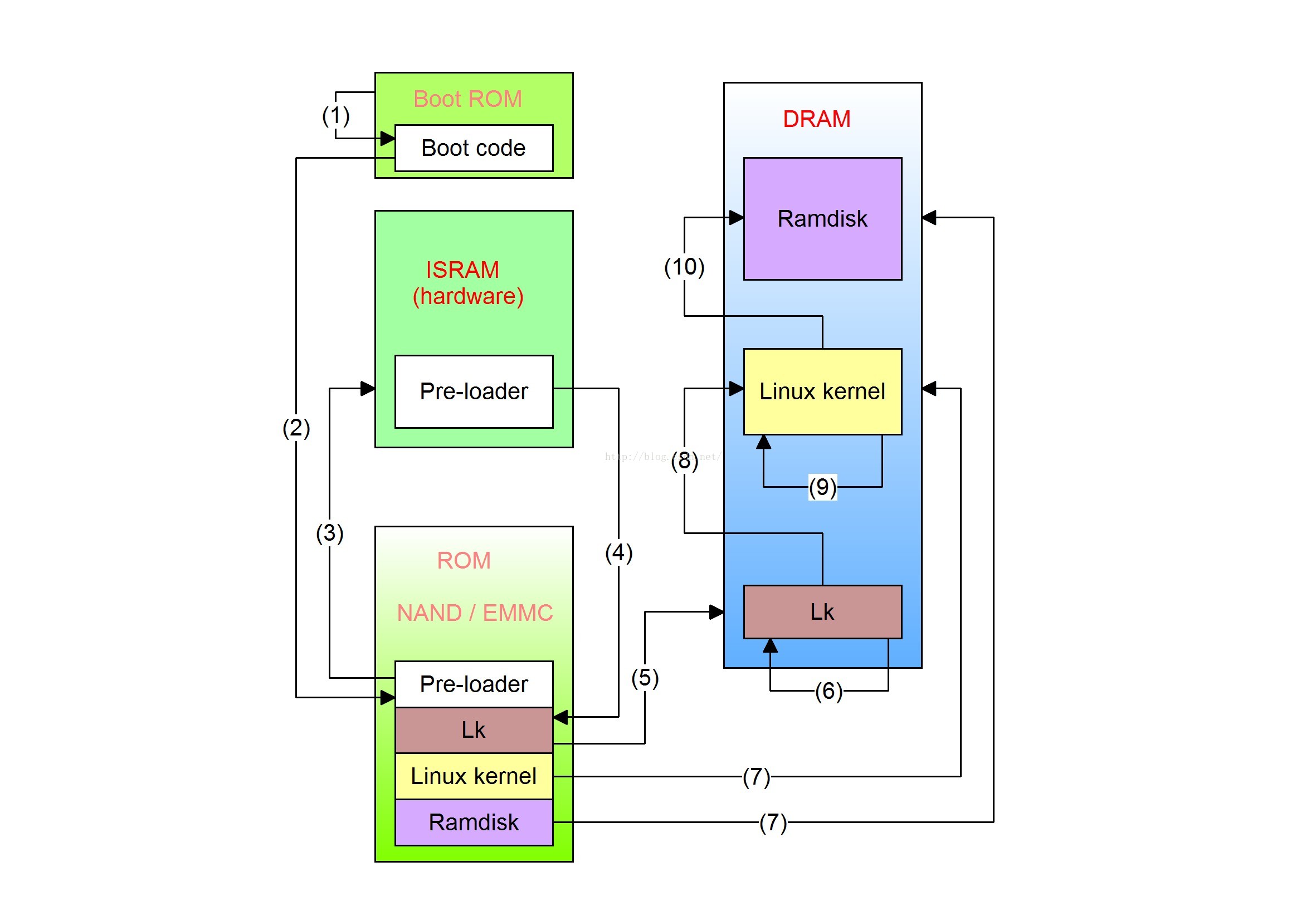
If the platform does not implement EL3(atf), the pre-loader loads lk directly:
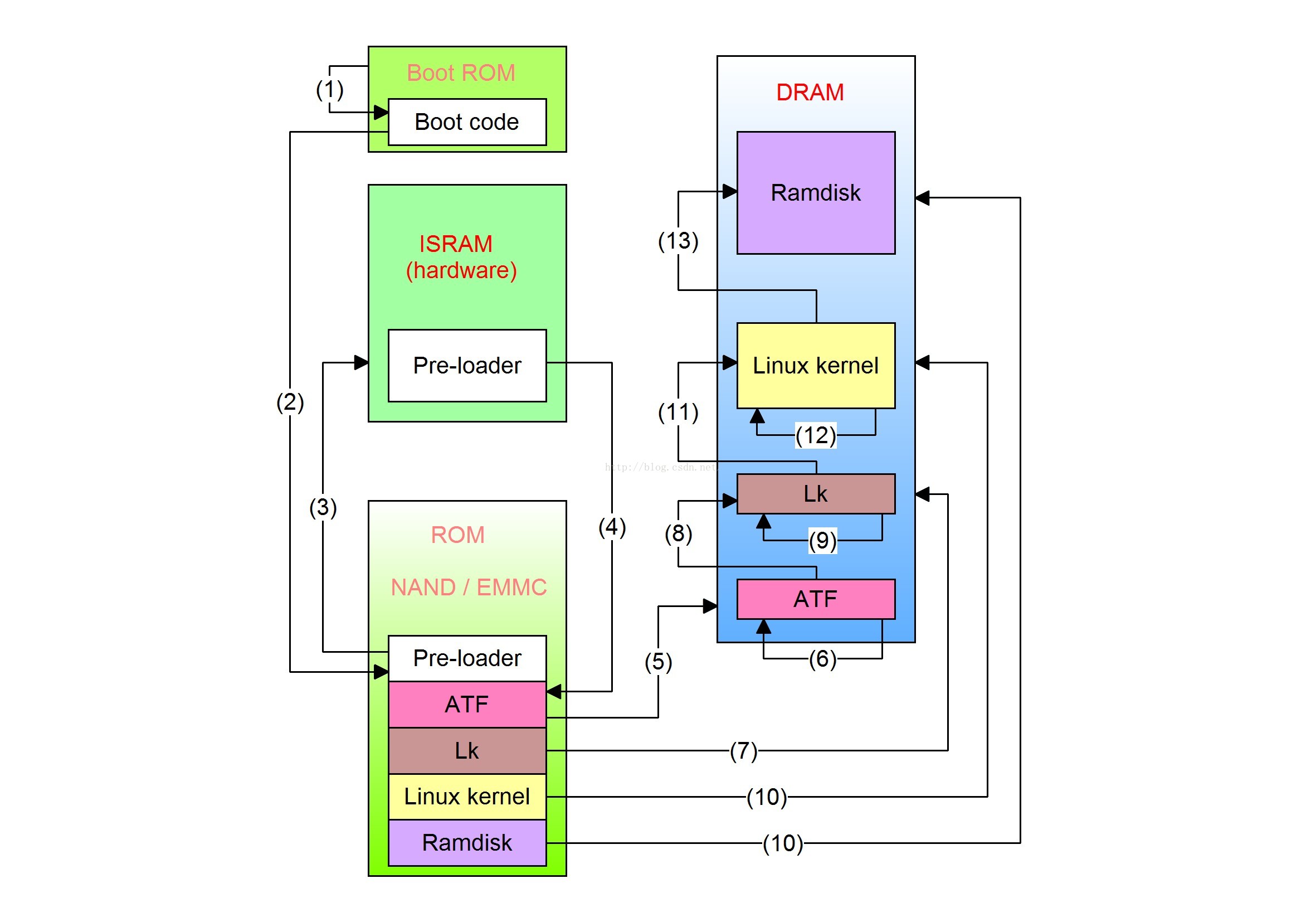
If the platform implements EL3, you need to load the ATF first and then load the lk by the ATF:
The bootloader starts in two phases.One is the pre-loader loading lk (u-boot) phase, and the other is the lk loading kernel phase.. The following is a brief description of the loading process of the first phase.
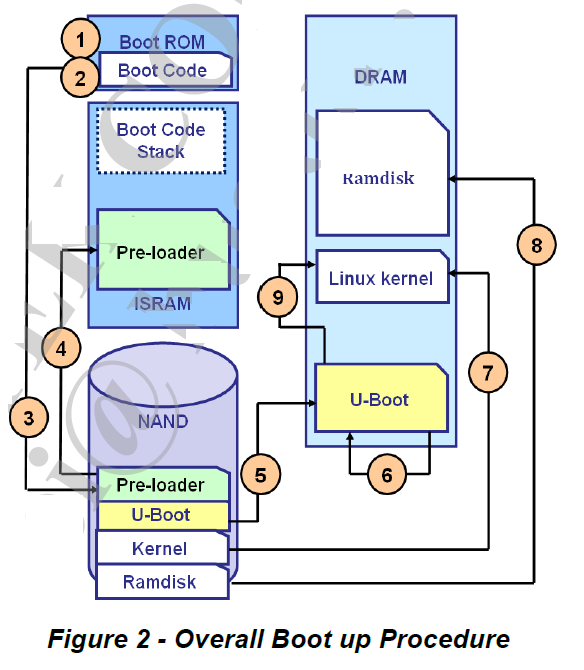
1-3: After the device is powered on, jump to the boot code in the Boot ROM (not flash) to load the pre-loader into ISRAM, because the current DRAM (RAM is divided into SRAM and DRAM, simply SRAM is the cache. , DRAM is ordinary memory) is not ready, so first load the pre-loader into the ISRAM (Internal SRAM) inside the chip.
4-6: After the pre-loader initializes the DRAM, it loads the lk from the flash (nand/emmc) into the DRAM;
7-8: Decompress bootimage into ramdisk and kernel and load into DRAM, initialize dtb;
9-11: lk jumps to kernl initialization, after the kernel initialization is completed, fork out the init process, and then pulls up the init program in ramdisk, enters user space initialization, init process forks out zygote process.. until the wholeAndroidThe startup is complete.
2, from pre-loader to lk (mt6580 as an example)
The main thing Pre-loader does is to initialize some hardware, such as: UART, GPIO, DRAM, TIMER, RTC, PMIC, etc., to establish the most basic operating environment, the most important thing is to initialize DRAM.
Timing diagram:

Click for larger image
The source code process is as follows:
-
./bootloader/preloader/platform/mt6580/src/init/init.s -
.section .text.start -
... -
.globl _start -
... -
/* set the cpu to SVC32 mode */ -
MRS r0,cpsr -
BIC r0,r0,#0x1f -
ORR r0,r0,#0xd3 -
MSR cpsr,r0 -
/* disable interrupt */ -
MRS r0, cpsr -
MOV r1, #INT_BIT -
ORR r0, r0, r1 -
MSR cpsr_cxsf, r0 -
... -
setup_stk : -
/* setup stack */ -
LDR r0, stack -
LDR r1, stacksz -
... -
entry : -
LDR r0, =bldr_args_addr -
/* Jump to C code main entry */ -
B main
The main thing in init.s is to switch the system to management mode (svc) (if the platform has el3, then the pre-loader runs on el3, otherwise it runs on el1), irq/fiq is disabled, stack is set, etc., then jump to c The code main function entry.
Enter the source code analysis.
-
./bootloader/preloader/platform/mt6580/src/core/main.c -
void main(u32 *arg) -
{ -
struct bldr_command_handler handler; -
u32 jump_addr, jump_arg; -
/* get the bldr argument */ -
bldr_param = (bl_param_t *)*arg; -
// Initialize uart -
mtk_uart_init(UART_SRC_CLK_FRQ, CFG_LOG_BAUDRATE); -
// There are a lot of things done here, including various platform hardware (timer, pmic, gpio, wdt...) initialization work. -
bldr_pre_process(); -
handler.priv = NULL; -
handler.attr = 0; -
handler.cb = bldr_cmd_handler; -
// Here is the information to get the startup mode and save it to the global variables g_boot_mode and g_meta_com_type. -
BOOTING_TIME_PROFILING_LOG("before bldr_handshake"); -
bldr_handshake(&handler); -
BOOTING_TIME_PROFILING_LOG("bldr_handshake"); -
// The following is related to secro img, which is strongly related to platform design. -
/* security check */ -
sec_lib_read_secro(); -
sec_boot_check(); -
device_APC_dom_setup(); -
BOOTING_TIME_PROFILING_LOG("sec_boot_check"); -
/* If EL3 has been implemented, then tz pre-initializes */ -
#if CFG_ATF_SUPPORT -
trustzone_pre_init(); -
#endif -
/* bldr_load_images -
The thing to do with this function is to load lk from the specified location in ROM to DRAM. You can see the specific information in the boot log: -
[PART] load "lk" from 0x0000000001CC0200 (dev) to 0x81E00000 (mem) [SUCCESS] -
Here is the specific address of the jump to DRAM, detailed analysis below. -
*/ -
if (0 != bldr_load_images(&jump_addr)) { -
print("%s Second Bootloader Load Failed\n", MOD); -
goto error; -
} -
/* -
The implementation of this function is platform_post_init, the thing to do here is actually relatively simple, is through -
Hw_check_battery to determine whether there is a battery in the current system (determine whether there is a battery ntc foot to distinguish) -
If it doesn't exist, it will get stuck in while(1), so sometimes debugging in es stage -
Need to connect to the power supply debugging, you need to change the logic inside to start normally -
*/ -
bldr_post_process(); -
// atf is officially initialized and implemented using a unique system call. -
#if CFG_ATF_SUPPORT -
trustzone_post_init(); -
#endif -
/* Jumps the parameters of the incoming lk, including boot time/mode/reason, etc. -
The platform_set_boot_args function gets. -
*/ -
jump_arg = (u32)&(g_dram_buf->boottag); -
/* Execute the jump system call, jump from pre-loader to lk,
If you realize the EL3 situationMore complicated, you need to jump to EL3 initialization first, then jump back to lk, pre-loader is executed in EL3, LK is executed in EL1)
This information can be seen similarly from the log: [BLDR] jump to 0x81E00000 [BLDR] <0x81E00000>=0xEA000007 [BLDR] <0x81E00004>=0xEA0056E2 */ #if CFG_ATF_SUPPORT /* 64S3,32S1,32S1 (MTK_ATF_BOOT_OPTION = 0) * re -loader jump to LK directly and then LK jump to kernel directly */ if ( BOOT_OPT_64S3 == g_smc_boot_opt && BOOT_OPT_32S1 == g_lk_boot_opt && BOOT_OPT_32S1 == g_kernel_boot_opt) { print("%s 64S3,32S1,32S1, jump to LK\n" , MOD); bldr_jump(jump_addr, jump_arg, sizeof(boot_arg_t)); } else {// If el3 is implemented using aarch64, jump to atf. print("%s Others, jump to ATF\n", MOD); bldr_jump64 (jump_addr, jump_arg, sizeof(boot_arg_t)); } #else bldr_jump(jump_addr, jump_arg, sizeof(boot_arg_t)); #endif // If you do not get jump_addr, print an error message and enter while(1) wait. error: Platform_error_handler(); }
Summary of the main function:
1, various hardware initialization (uart, pmic, wdt, timer, mem..);
2. Obtain the system startup mode, etc., and save it in the global variable;
3, Security check, related to secro.img;
4. If the system has implemented el3, enter tz initialization;
5. Get the address (fixed value) loaded by lk into the DRAM, and then find the address of the lk partition from the ROM. If jump_addr is not found, then goto error;
6, battery check, if there is no battery will fall into while (1);
7, jump to lk (if there is implementation of el3, it will jump to el3, then back to lk)
3. Analysis of key functions
bldr_load_images
The main function of the function is to find the address of the lk partition and the address that lk loads into the DRAM, and prepare the jump to lk for execution.The following source code analysis:
-
static int bldr_load_images(u32 *jump_addr) -
{ -
int ret = 0; -
blkdev_t *bootdev; -
u32 addr = 0; -
char *name; -
u32 size = 0; -
u32 spare0 = 0; -
u32 spare1 = 0; -
... -
/* This address is a fixed value and can be found to be defined in: -
./bootloader/preloader/platform/mt6580/default.mak:95: -
CFG_UBOOT_MEMADDR := 0x81E00000 -
From the log you can see: -
[BLDR] jump to 0x81E00000 -
*/ -
addr = CFG_UBOOT_MEMADDR; -
/* Then go to the ROM and find the partition address where lk is located */ -
ret = bldr_load_part("lk", bootdev, &addr, &size); -
if (ret) -
return ret; -
*jump_addr = addr; -
} -
// This function logic is very simple, so you don't need to say more. -
int bldr_load_part(char *name, blkdev_t *bdev, u32 *addr, u32 *size) -
{ -
part_t *part = part_get(name); -
if (NULL == part) { -
print("%s %s partition not found\n", MOD, name); -
return -1; -
} -
return part_load(bdev, part, addr, 0, size); -
} -
// The real load implementation is in the part_load function. -
int part_load(blkdev_t *bdev, part_t *part, u32 *addr, u32 offset, u32 *size) -
{ -
int ret; -
img_hdr_t *hdr = (img_hdr_t *)img_hdr_buf; -
part_hdr_t *part_hdr = &hdr->part_hdr; -
gfh_file_info_t *file_info_hdr = &hdr->file_info_hdr; -
/* specify the read offset */ -
u64 src = part->startblk * bdev->blksz + offset; -
u32 dsize = 0, maddr = 0; -
u32 ms; -
// Retrieve the partition header is correct. -
/* retrieve partition header. */ -
if (blkdev_read(bdev, src, sizeof(img_hdr_t), (u8*)hdr,0) != 0) { -
print("[%s]bdev(%d) read error (%s)\n", MOD, bdev->type, part->name); -
return -1; -
} -
if (part_hdr->info.magic == PART_MAGIC) { -
/* load image with partition header */ -
part_hdr->info.name[31] = '\0'; -
/* -
Various information about the output partition, you can see from the log: -
[PART] Image with part header -
[PART] name : lk -
[PART] addr : FFFFFFFFh mode : -1 -
[PART] size : 337116 -
[PART] magic: 58881688h -
*/ -
print("[%s]Img with part header\n", MOD); -
print("[%s]name:%s\n", MOD, part_hdr->info.name); -
print("[%s]addr:%xh\n", MOD, part_hdr->info.maddr); -
print("[%s]size:%d\n", MOD, part_hdr->info.dsize); -
print("[%s]magic:%xh\n", MOD, part_hdr->info.magic); -
maddr = part_hdr->info.maddr; -
dsize = part_hdr->info.dsize; -
src += sizeof(part_hdr_t); -
memcpy(part_info + part_num, part_hdr, sizeof(part_hdr_t)); -
part_num++; -
} else { -
print("[%s]%s img not exist\n", MOD, part->name); -
return -1; -
} -
// If maddr is not defined, then the address incoming addr is used. -
if (maddr == PART_HEADER_MEMADDR/*0xffffffff*/) -
maddr = *addr; -
if_overlap_with_dram_buffer((u32)maddr, ((u32)maddr + dsize)); -
ms = get_timer(0); -
if (0 == (ret = blkdev_read(bdev, src, dsize, (u8*)maddr,0))) -
*addr = maddr; -
ms = get_timer(ms); -
/* If all goes well, it will print out key information: -
[PART] load "lk" from 0x0000000001CC0200 (dev) to 0x81E00000 (mem) [SUCCESS] -
[PART] load speed: 25324KB/s, 337116 bytes, 13ms -
*/ -
print("\n[%s]load \"%s\" from 0x%llx(dev) to 0x%x (mem) [%s]\n", MOD, -
part->name, src, maddr, (ret == 0) ? "SUCCESS" : "FAILED"); -
if( ms == 0 ) -
ms+=1; -
print("[%s]load speed:%dKB/s,%d bytes,%dms\n", MOD, ((dsize / ms) * 1000) / 1024, dsize, ms); -
return ret; -
}
bldr_post_process
The main thing that the function does is to check if there is a battery from pmic, if not, wait, the following source code analysis, relatively simple:
-
// It's just a layer. -
static void bldr_post_process(void) -
{ -
platform_post_init(); -
} -
// The focus is on this function: -
void platform_post_init(void) -
{ -
/* normal boot to check battery exists or not */ -
if (g_boot_mode == NORMAL_BOOT && !hw_check_battery() && usb_accessory_in()) { -
... -
pl_charging(1); -
do { -
mdelay(300); -
/* Check if the battery is present. If you use power debugging, you need to modify this function logic */ -
if (hw_check_battery()) -
break; -
/* Feed the dog to avoid being bitten by the dog over time */ -
platform_wdt_all_kick(); -
} while(1); -
/* disable force charging mode */ -
pl_charging(0); -
} -
... -
}
Intelligent Recommendation
Start from the MCU to the startup process to write Bootloader (top)
The BOOT of the development board is started from EFLASH (that is, Flash memory in the film). The corresponding settings are also required in the keil. Bootloader to be written next is written to EFLA...
Start from the MCU to the startup process to write bootloader (middle)
The startup process of the MCU power -on has been analyzed above. This article attempts to write a simple Bootloader and an app that implements CAN communication, and pave the way for us to try to wri...
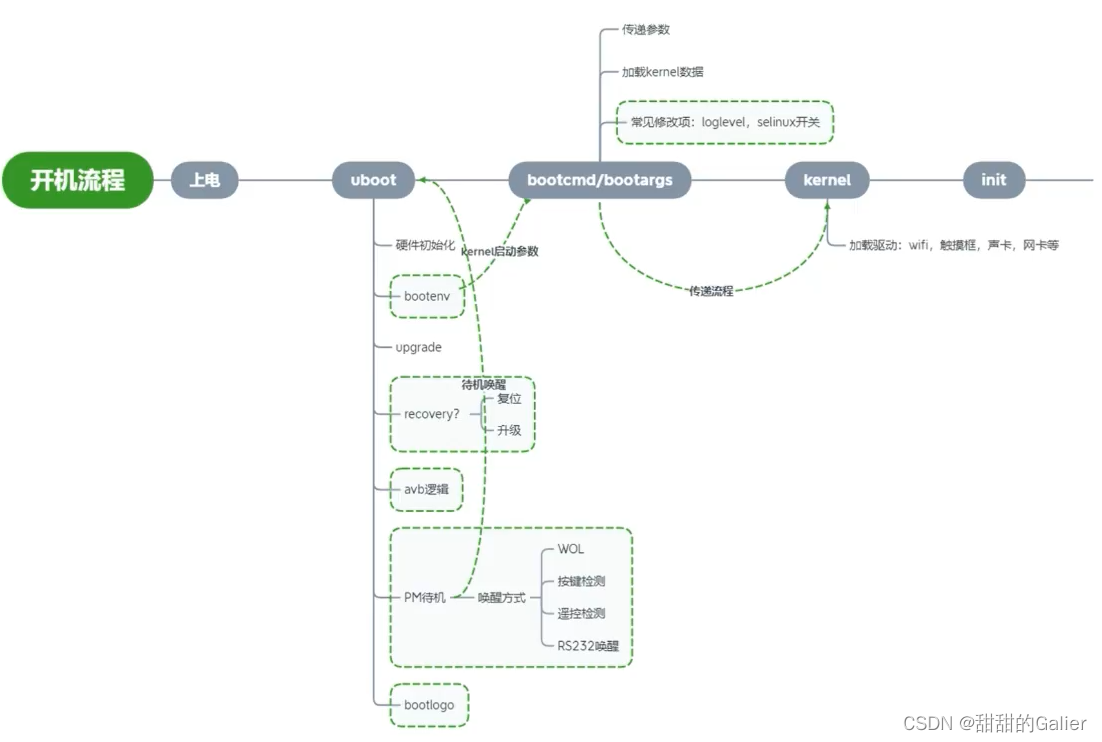
Introduce BootLoader, PM, kernel and the overall process of system startup
BootLoader, PM, kernel and the overall process of system startup 1. Overall start-up process 2. Related subsystems 3. What is done in each link? 4. Introduction to bootloader 1. Commonly used bootload...
Bootloader startup parameter passing
Arm platform The arch/arm/kernel/head.S file defines the parameter transfer requirements for the bootloader and kernel: So in the main entry function of the kernel, you need to pass 3 parameters, r0/r...

Bootloader startup and function
Article Directory Introduction to Bootloader S5P6818 startup process (one pass, one pass) Install the uboot burning tool Introduction to Bootloader Bootloader can be interpreted as starting the boot p...
More Recommendation
MTK platform startup process, based on LK, mt6761 to establish a startup mind map
Start the assembly line: BootRom -----------> Preloader ----------->LK ----------->linux kernel Here only boot to the kernel, the init process to the Android system to be summarized ne...

[Embedded Development] Bootloader Detailed (Code Environment | ARM Startup Process | uboot Workflow | Architecture Design)...
Author : Han Yuliang blog address : Reprinted please famous source Related resources download: -- U-boot source: -- S3C2440 documentation : --S5PV210_iROM_ApplicationNote_Preliminary_20091126 Document...
bootloader pass startup parameters (b)
1.dtb how is passed to the kernel of? First base dtb is packaged into the kernel with the boot.img, dtbo a separate partition is stored, transmitted to the kernel after integration after loading bootl...
Bootloader startup analysis of xv6 system
Bootloader startup analysis Refer to Appendix B of xv6 https://github.com/ranxian/xv6-chinese/blob/master/content/AppendixB.md The behavior of the hardware after the computer starts Always curious abo...
Introduction to the bootloader process
Bootloader overview From the perspective of software, an embedded Linux system is usually divided into four levels: bootloader, Linux kernel, file system, and user application. In linux, the bootloade...